new posts in all blogs
Viewing: Blog Posts Tagged with: privacy, Most Recent at Top [Help]
Results 1 - 25 of 45
How to use this Page
You are viewing the most recent posts tagged with the words: privacy in the JacketFlap blog reader. What is a tag? Think of a tag as a keyword or category label. Tags can both help you find posts on JacketFlap.com as well as provide an easy way for you to "remember" and classify posts for later recall. Try adding a tag yourself by clicking "Add a tag" below a post's header. Scroll down through the list of Recent Posts in the left column and click on a post title that sounds interesting. You can view all posts from a specific blog by clicking the Blog name in the right column, or you can click a 'More Posts from this Blog' link in any individual post.

By: Kim Schwenk,
on 5/2/2016
Blog:
Lux Mentis, Lux Orbis
(
Login to Add to MyJacketFlap)
JacketFlap tags:
victorian,
privacy,
Feature,
letter writing,
Correspondence,
chooseprivacy,
cross-writing,
victorian cross-writing,
Add a tag
Living in a time of unprecedented information surveillance, also lends itself to an unbelievable amount of information privilege for much of the “democratized” world. We feign emotions with character smiley faces and iconography as our communications float rapidly over a network of intangible speeds, sometimes coated with an algorithm of encryption and sometimes, not. Identity is, at best, both catastrophic and creative. So as we celebrate and converse about National Privacy Week, it is sort of interesting to think about privacy, not only in the way we might shroud our communications, but also in terms of economics, commodity and modality.
In the early 19th century, the postal system was financially demanding for some people [not unnecessarily unlike today] *and* was the scarcity of paper. Tom Standage writes in the Victorian Internet [1998]: “In the nineteenth century, letter writing was the only way to communicate with those living at a distance. However, prior to 1840, the post was expensive. Postal charges grew high in England due to the inflationary pressure of the Napoleonic Wars. Different from the way mail operates today, the burden of payment fell to the receiver, not the sender; prepayment was a social slur on the recipient. One had to be financially solvent to receive a letter. If the recipient could not afford to pay for a letter, it was returned to sender. Any reader of Jane Austen’s Emma (1815) knows that to save costs, cross writing was common — a writer turned his or her letter horizontally and “crossed” (or wrote over) the original text at a right angle rather than use an additional sheet of paper. Folded letters with a wax seal may look quaint, but like cross writing, this was also a pre-1840s cost cutting measure since that same missive, posted in an envelope, would receive double charge.”
A cost-cutting measure indeed, however, and not insignificant it created a system of visual encryption one might employ for secrecy, but also as a device of post-modernity and compositional ingenuity. In 1819, John Keats constructed a crossed letter discussing both the merit of prescriptive living for labor workers, only to be written over at an angle by his poem, Lamia, about a man who falls in love with a snake disguised as a woman. “The non-linearity of meaning is generated as an excess against the unidirectional drive of information, like the snakes that weave around the staff of a caduceus or the turbulent wake of a forward-moving ship; meaning is the snake and the wake of information.” [1] Quite a metaphor to create, as a perception of romanticism, in era of rapid change. Sound familiar? When in doubt, think smart, choose privacy.
We have a suite of 19th century letters in our collection of cross-writing, or “cross-hatching,” check out the images:
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting3-150x150.jpeg)
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting2-150x150.jpeg)
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting1-150x150.jpeg)
#chooseprivacy
[1] Livingston, Ira. Arrow of Chaos: Romanticism and Postmodernity.

By: Shelf-employed,
on 2/22/2016
Blog:
Shelf-employed
(
Login to Add to MyJacketFlap)
JacketFlap tags:
YA,
adult,
nonfiction,
Vietnam War,
privacy,
J,
newspapers,
national security,
Daniel Ellsberg,
Add a tag
 Most Dangerous: Daniel Ellsberg and the Secret History of the Vietnam War by Steve Sheinkin (2015) Roaring Brook Press
Most Dangerous: Daniel Ellsberg and the Secret History of the Vietnam War by Steve Sheinkin (2015) Roaring Brook Press
As he did with the spy, Harry Gold, in Bomb: The Race to Build—and Steal—the World’s Most Dangerous Weapon, Steven Sheinkin uses one man to tell a much larger story in Most Dangerous: Daniel Ellsberg and the Secret History of the Vietnam War. That man is the infamous leaker of the so-called Pentagon Papers, Daniel Ellsberg. A veteran himself, and a former Pentagon employee, Ellsberg initially believed that the war in Vietnam was a noble cause. However, the more he learned, the less he believed so. Eventually, based on the information to which he was privy and the US populace was not, he changed his mind completely.
Whether you believe Edward Snowden to be a patriotic whistleblower or a traitorous leaker, and whether you believe that Apple's refusal to hack into the phone of the San Bernardino murderers is reprehensible or ethical, it cannot be denied that these are weighty matters worthy of national discussion. In the time of Daniel Ellsberg, people read newspapers and watched a generally unbiased nightly newscast. In contrast, many people today derive their news from "sound bites," political analysts, and partisan news stations. These issues deserve more thoughtful consideration.
While
Most Dangerous is an excellently researched biographical and historical account, and can be appreciated for that aspect alone, Steve Sheinkin's book also will also promote reflection on the nature of national security, personal privacy, democracy, freedom of the press, and foreign intervention. We have been on very similar ground before.
Selected quotes:
page 149
"They all drove to the Capitol for the traditional outdoor inauguration ceremony. Johnson watched Nixon take the oath of office, wondering what lay ahead. "I reflected on how inadequate any man is for the office of the American Presidency," he later recalled. "The magnitude of the job dwarfs every man who aspires to it.""
page 160
"He had often heard antiwar protesters shouting that Americans were fighting on the wrong side of the Vietnam War. They were missing the point. "It wasn't that we were on the wrong side," Ellsberg concluded, "We were the wrong side.""
FBI agents began questioning the Ellsbergs friends and relatives. They even attempted to obtain Patricia Ellsberg's dental records, but her dentist refused to cooperate. Nixon's operatives broke into the office of Daniel Ellsberg's doctor in a failed attempt to steal his medical records. They were searching for anything to use in a campaign to discredit Ellsberg.
page 263
"Psychologically, it's not so bothersome, because we believe in what we're doing," Patricia Ellsberg said about the feeling of being watched by one's own government. "But I think it's troublesome for the country that there is surveillance of citizens, and that the right of privacy is being threatened."
Read an excerpt from Most Dangerous here.Awards and accolades:
Other Steve Sheinkin books reviewed on Shelf-employed


By: Amy Jelf,
on 12/4/2015
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
quiz,
Law,
freedom of speech,
freedom of the press,
privacy,
human rights,
VSI,
Very Short Introductions,
*Featured,
Quizzes & Polls,
human rights law,
VSI online,
Andrew Clapham,
Human Rights VSI,
Human Rights: A Very Short Introduction,
vsi quiz,
Add a tag
In the last two hundred years, the concept of human rights has gained prevalence in society. We can define our rights in terms of freedom of speech, privacy, and to be treated humanely, but where did these ideas come from? Do you think you know your human rights?
The post Do you know your human rights? [Quiz] appeared first on OUPblog.

By: Fiona Parker,
on 10/13/2015
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Anton Chekhov,
*Featured,
oxford journals,
privacy law,
Christopher Kuner,
data privacy,
Data Privacy Law,
International Data Privacy Law,
commercial law,
commlaw,
Literature,
Law,
internet,
Journals,
Social Networking,
privacy,
social media,
chekhov,
Add a tag
Defining “privacy” has proven akin to a search for the philosopher’s stone. None of the numerous theories proposed over the years seems to encompass all the varied facets of the concept. In considering the meaning of privacy, it can be fruitful to examine how a great artist of the past has dealt with aspects of private life that retain their relevance in the Internet age.
The post A Chekhovian view of privacy for the internet age appeared first on OUPblog.

By: Hannah Paget,
on 5/28/2015
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
freedom,
Sociology,
Politics,
privacy,
surveillance,
Social Sciences,
liberal democracy,
UKpophistory,
edward snowden,
open university,
OU,
Birkett,
David vincent,
I hope I don't intrude,
Sir James Graham,
Books,
*Featured,
Add a tag
In its recent report, Privacy and Security: A modern and transparent legal framework, the Parliamentary Intelligence and Security Committee pondered on the scale of public concern about digital surveillance. A feature of the current controversy is its narrow chronology. The decades before 9/11 correspond to the medieval period and the centuries before the internet are lost in the mists of time. The legislation that controls the behaviour of the security agencies, particularly the Acts of 1989, 1994 and 2000, is generally seen as obsolete.
The post Surveillance and privacies appeared first on OUPblog.

By: ChloeF,
on 3/20/2015
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Books,
Privacy: A Very Short Introduction,
right to be forgotten,
Law,
Data,
privacy,
Media,
government,
security,
terrorism,
nsa,
VSI,
Very Short Introductions,
National Security Agency,
*Featured,
privacy law,
Online products,
raymond wacks,
data protection,
Add a tag
In the 1960s British comedy radio show, Beyond Our Ken, an old codger would, in answer to various questions wheel out his catchphrase—in a weary, tremulous groan—‘Thirty Five Years!’ I was reminded of this today when I realized that it is exactly 35 years ago that my first book on privacy was published. And how the world has changed since then!
The post Is privacy dead? appeared first on OUPblog.

By: Elizabeth Gorney,
on 8/9/2014
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Books,
Technology,
facebook,
digital,
privacy,
Media,
social media,
online,
clients,
donuts,
psychotherapy,
apps,
client,
APA,
app,
Psychotherapist,
*Featured,
American Psychological Association,
Psychology & Neuroscience,
APA2014,
Jan Willer,
The Beginning Psychotherapist's Companion,
therapist patient relationship,
psychotherapists,
psychotherapist’s,
willer,
Add a tag
By Jan Willer
Social media and other technologies have changed how we communicate. Consider how we coordinate events and contact our friends and family members today, versus how we did it 20 or 30 years ago. Today, we often text, email, or communicate through social media more frequently than we phone or get together in person.
Now contrast that with psychotherapy, which is still about two people getting together in a room and talking. Certainly, technology has changed psychotherapy. There are now apps for mental health issues. There are virtual reality treatments. Psychotherapy can now be provided through videoconferencing (a.k.a. telehealth). But still, it’s usually simply two people talking in a room.
Our psychotherapy clients communicate with everyone else they know through multiple technological platforms. Should we let them “friend” us on social media? Should we link to them on professional networking sites? Is it ok to text with them? What about email? When are these ok and not ok?

Social Media Explained (with Donuts). Uploaded by Chris Lott. CC-BY-2.0 via Flickr.
Some consensus is emerging about these issues. Experts agree that psychotherapists should not connect with current or former clients on social media. This is to help preserve the clients’ confidentiality. Emailing and texting are fine for communicating brief messages about the parameters of the session, such as confirming the appointment time, or informing the psychotherapist that the client is running late. Research has shown that emotional tone is frequently miscommunicated in texting and email, so emotion-laden topics are best discussed during the session.
How do we learn about new people we’ve met? In the past, we’d talk directly to them, and maybe also talk to people we knew in common. Now everyone seems to search online for everyone else. This happens frequently with first dates, college applicants, and job applicants.
Again, contrast this with psychotherapy. Again, two people are sitting in a room, talking and learning about each other. When is it ok for a psychotherapist to search for information about a client online? What if the psychotherapist discovers important information that the client withheld? How do these discoveries impact the psychotherapy?
No clear consensus has emerged on these issues. Some experts assert that psychotherapists should almost never search online for clients. Other experts respond that it is unreasonable to expect that psychotherapists should not access publicly available information. Others suggest examining each situation on a case-by-case basis. One thing is clear: psychotherapists should communicate with their clients about their policies on internet searches. This should be done in the beginning of psychotherapy, as part of the informed consent process.
When we’ve voluntarily posted information online–and when information about us is readily available in news stories, court documents, or other public sources–we don’t expect this information to be private. For this reason, I find the assertion that psychotherapists can access publically available information to be more compelling. On my intake forms, I invite clients to send me a link to their LinkedIn profile instead of describing their work history, if they prefer. If a client mentions posting her artwork online, I’ll suggest that she send me a link to it or ask her how to find it. I find that clients are pleased that I take an interest.
What about the psychotherapist’s privacy? What if the client follows the psychotherapist’s Twitter account or blog? What if the client searches online for the psychotherapist? What if the client discovers personal information about the psychotherapist by searching? Here’s the short answer: psychotherapists need to avoid posting anything online that we don’t want everyone, including our clients, to see.
Ways to communicate online continue to proliferate. For example, an app that sends only the word “Yo” was recently capitalized to the tune of $2.5 million and was downloaded over 2 million times. Our professional ethics codes are revised infrequently (think years), while new apps and social media are emerging monthly, even daily. Expert consensus on how to manage these new communications technologies emerges slowly (again, think years). But psychotherapists have to respond to new communications technologies in the moment, every day. All we can do is keep the client’s well-being and confidentiality as our highest aspiration.
Jan Willer is a clinical psychologist in private practice. For many years, she trained psychology interns at the VA. She is the author of The Beginning Psychotherapist’s Companion, which offers practical suggestions and multicultural clinical examples to illustrate the foundations of ethical psychotherapy practice. She is interested in continuing to bridge the notorious research-practice gap in clinical psychology. Her seminars have been featured at Northwestern University, the University of Chicago, and DePaul University.

Subscribe to the OUPblog via email or RSS.
Subscribe to only psychology articles on the OUPblog via email or RSS.
The post My client’s online presence appeared first on OUPblog.

A year ago today, we joined the world in shock on learning that governments were spying on internet users around the world. Tapping internet service providers’ undersea cables, intentionally and secretly weakening encryption products, surreptitiously collecting everything from call metadata to photos sent over the internet by US citizens — nothing was off limits.
Just as troubling as the revelations themselves is the fact that since last summer, little if anything has changed. Despite a lot of rhetoric, our three branches of government in the United States have not made many concrete steps toward truly protecting citizens from unchecked government surveillance.
Automattic has been a strong supporter of efforts to reform government surveillance. We’ve supported reform legislation in Congress, and participated in the Day We Fight Back, earlier this year. More importantly, we aim to make our own legal processes for securing the information our users entrust to us as transparent and protective as possible.
Be the change you want to see in the world — that’s why we’re joining the many other companies who are participating today in Reset the Net. In the face of intrusive surveillance, we believe that everyone in the tech community needs to stand up and do what they can, starting with their own sites and platforms. For us, that means working to secure the connection between users and our websites. We’ll be serving all *.wordpress.com subdomains only over SSL by the end of the year.
If we’ve learned anything over the past year, it’s that encryption, when done correctly, works. If we properly encrypt our sites and devices, we can make mass surveillance much more difficult.
We’re happy to be taking these steps and hope that the coming year brings real reform to end mass surveillance.
Filed under:
Community 

Today, a broad coalition of interest groups, websites, and people around the world are joining together to fight back against government surveillance. We’re supporting the “Day We Fight Back” on WordPress.com and have created a banner that you can easily add to your WordPress.com blog to get involved, too.
The “Stop NSA Surveillance” banner shows support for this important cause and provides a link to a page of resources to help visitors to contact members of the US Congress to support much needed anti-surveillance legislation. For more information, please visit thedaywefightback.org.
How to add the banner to your site
Here’s how to add the banner to your site in three steps:
- In your WordPress.com dashboard, go to Settings → Protest NSA Surveillance.
- Click on the checkbox labelled Protest Enabled.
- Click on the Save Changes button for the change to take effect.
The banner will remain on your site until midnight on your blog’s time zone. Here’s what it will look like:

Filed under:
Community,
Privacy 


For some reason last year I didn’t do my annual roundup of Banned Books Week websites. Here is a link to the source of the image above which is from the New Yorker’s article about the JD Salinger-evocative book 60 Years Later, Coming Through the Rye which is illegal to sell in the US. You can find more news articles about that situation at the author’s small Wikipedia page. You can look at past posts on this topic by checking out the bannedbooksweek tag here or here is a list of the annual posts: 2000, 2001, 2002, 2003, 2004, 2006, 2007, 2008, 2009, 2010 and 2011. I skipped 2005 and 2012.
As usual, you get a neat real-time look at what’s going on by following the Twitter hashtag. Do NOT look at the bbw twitter hashtag as I mistakenly did last night. As usual there are two “main” sites the ALA site at ala.org/bbooks and the bannedbooksweek.org site which is really nice looking this year. The BannedBooksWeek Twitter account is still moribund which is a damned shame. The Virtual Read Out doesn’t seem to have any new videos this year… yet?
Please remember if you are a librarian who has a book that is challenged, report it to the ALA so they can keep track of it.
Here is the list of organizations who are co-sponsors. Let’s look at their websites.
PEN American Center – has this post outlining what they’re up to this week and they appear to be extended their activities for a full month and this blog post (some reflections by Nick Burd, an author whose book had been challenged) is a well-written little capsule piece.
The language of the censor is the language of the tyrant, the absolutist, the one with no vision. It is the antithesis of art because it assumes that there is only one perspective, one reality, and that anything that fails to rhyme with it is a sin against nature. But the real sin against nature is to suffocate personal truths and experiences with wobbly doctrine and to disguise it as morally just. Art— particularly literature—exists to show us there are as many worlds as there are people. Each of these worlds come with its own laws. These laws vary from person to person, but if there is one that they have in common it is to share your truth. We owe it to our humanity and our short time among other humans to respect the truths that are shared with us. – Nick Burd
Websites are working and the word is getting out. I was pleased with this year’s collections of content. What I’m concerned about, as per usual, are challenges and censorship that don’t even reach the physical items on the library shelves. What about this Salinger book? Worldcat shows 40 copies of it, a handful of which are in the US, and the reviews of it haven’t been so great anyhow. But the idea that the book wasn’t obtained and removed, it was never obtained in the first place (as we see with so much born-digital content that we can’t even get in lendable format) opens a door to all new ways that libraries can not get books. The old challenges (dirty cowboy? really? do not google that) remain and new ones appear.

Hello, I was away for the summer. It seems that there has been some activity. If you’re here because you heard about my The FBI Has Not Been Here signs, here is a link to the page where I first mentioned them, back in 2005 or so. Back when this idea was getting batted around it was originally because the USA PATRIOT Act was concerning people, the idea that if you even got a National Security Letter not only would it compel you to turn over records, but it also prevented you from telling anyone other than your legal counsel. This sort of sucked and so people fought back. Most notably the people from Library Connection in Connecticut who got the gag order part of the USA PATRIOT Act declared unconstitutional. And you may have read about Brewster Kahle talking in the New Yorker about what it’s like to get a National Security Letter. Brewster is one of the strongest advocate for the right to privacy (and libraries’ right to defend their patrons’ privacy) and even he was sort of freaked out by this. Now that we’re looking into the face of the NSA looking into damned near everything and their heavy-handed tactics to get corporations to comply with them, it’s almost quaint thinking that we were just afraid of the USA PATRIOT Act. You can read more about the idea of “warrant canaries” here. I certainly didn’t think them up, just got a little traction with this one. Oh hey look there is this image over on Wikipedia’s warrant canary article. That’s nice.

By: Alice,
on 1/28/2013
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Current Affairs,
privacy,
processing,
*Featured,
Law & Politics,
oxford journals,
Christopher Kuner,
Corporate Compliance and Regulation,
data privacy,
Data Privacy Law,
European Data Protection Law,
International Data Privacy Law,
Transborder Data Flow Regulation,
apec,
kuner,
ecowas,
“data,
Add a tag
By Christopher Kuner
Tension between different regulatory systems has long existed in certain areas (think of the disagreements between EU and US competition regulators regarding the aborted GE-Honeywell merger in the early 2000s). A similar power struggle is currently underway between different legal regimes regulating the collection, processing, and transfer of personal data (variously referred to in different legal systems as “data protection”, “data privacy”, or “information privacy” law), one that will shape the world in the 21st century.
 Data protection law has traditionally been viewed as a dreary subject of interest only to a few specialists. But whether it involves filling out government forms, purchasing items on the web, communicating with friends and relatives online, or checking in for a flight, almost every activity we engage in nowadays involves the processing of personal data. The growing importance of data processing is reflected in the large number of countries (approximately 100) around the world that have enacted data protection laws, and the countries and international organisations (including the European Union, the OECD, and the United States) that are currently in the process of revising them to meet the challenges posed by globalisation and the rapid growth of the Internet.
Data protection law has traditionally been viewed as a dreary subject of interest only to a few specialists. But whether it involves filling out government forms, purchasing items on the web, communicating with friends and relatives online, or checking in for a flight, almost every activity we engage in nowadays involves the processing of personal data. The growing importance of data processing is reflected in the large number of countries (approximately 100) around the world that have enacted data protection laws, and the countries and international organisations (including the European Union, the OECD, and the United States) that are currently in the process of revising them to meet the challenges posed by globalisation and the rapid growth of the Internet.
Much personal data routinely flows across national borders, and the same data processing may result in the application of multiple laws. The ease with which data flows internationally also means that data privacy law has become a point of competition between different legal systems, with each one striving to achieve the seemingly impossible goal of simultaneously protecting the privacy of individuals, striking a balance between privacy and other important values (e.g., public security), and furthering economic growth.
This competition has been most pronounced between the European Union, which has recently asserted that other countries should follow the “gold standard” of its data protection legislation, and the United States, which believes that its system is even better. Such international regulatory spats illustrate that nations too often view the subject largely as a way to score political points, and that they have failed to grasp some basic facts about the processing of personal data:
- Protection of data privacy is not just a transatlantic issue. Data protection laws have been enacted all over the world, including by regional organizations (APEC, ECOWAS, and others) and dozens of nations in Africa, Latin America, and Asia.
- It is also not just an online issue. Nearly every economic and social activity nowadays involves the processing of personal data, including the most basic ones. Too often regulatory attention focuses on the online “flavour of the month” (e.g., social networks, search engines, etc.), and fails to recognize that data processing has become embedded in every aspect of society.
- And it is not just an economic issue, but one that can help further important developmental goals as well. For example, the UN Secretary General has begun an initiative called “Global Pulse” involving projects such as the use of data analytics to better understand the global state of various infectious diseases, and using a centralized text messaging system to allow mobile phone users to report on people trapped under buildings following an earthquake, among others. Data protection law is currently not conceived to facilitate the large-scale use of data mining for purposes related to development, public health, and similar goals, but these uses will greatly increase in coming years, and will challenge our assumptions about the purposes and structure of regulation.
Part of the problem is that while data protection and privacy issues have global ramifications, the legal framework for them is still very much a matter of local or, at best, regional regulation. While some regional organizations (in particular the Council of Europe) are attempting to become more global, there are substantial differences in the way the subject is viewed in different countries and legal systems. In contrast to some other areas of the law, there is also a lack of legal instruments and institutions of a global scope covering privacy and data protection.
Legal regulation of data processing often stands in tension with economic pressures that encourage the processing and transfer of personal data, and political pressures that inhibit the development of coordinated and coherent regulation. States are only too happy to adopt legal requirements for the private sector that they are unwilling to comply with themselves (e.g., with regard to data processing for law enforcement purposes), and technology to process personal data advances faster than the law can keep up with.
From being considered a niche area, data protection law has evolved to the point that it is hard to find areas of human endeavour that it does not concern. The way that the struggles over data protection are resolved in the coming years will determine the kind of world we live in, and the kind of Internet we have.
 Dr. Christopher Kuner is editor-in-chief of the journal International Data Privacy Law. He is author of European Data Protection Law: Corporate Compliance and Regulation, and the forthcoming book Transborder Data Flow Regulation and Data Privacy Law in which he elaborates some of the topics discussed here. Dr. Kuner is Senior Of Counsel at Wilson Sonsini Goodrich & Rosati in Brussels, and an Honorary Fellow of the Centre for European Legal Studies, University of Cambridge.
Dr. Christopher Kuner is editor-in-chief of the journal International Data Privacy Law. He is author of European Data Protection Law: Corporate Compliance and Regulation, and the forthcoming book Transborder Data Flow Regulation and Data Privacy Law in which he elaborates some of the topics discussed here. Dr. Kuner is Senior Of Counsel at Wilson Sonsini Goodrich & Rosati in Brussels, and an Honorary Fellow of the Centre for European Legal Studies, University of Cambridge.
Combining thoughtful, high level analysis with a practical approach, International Data Privacy Law has a global focus on all aspects of privacy and data protection, including data processing at a company level, international data transfers, civil liberties issues (e.g., government surveillance), technology issues relating to privacy, international security breaches, and conflicts between US privacy rules and European data protection law.
Subscribe to the OUPblog via email or RSS.
Subscribe to only law and politics articles on the OUPblog via email or RSS.
Image credit: Laptop keyboard with fingerprint enlarged by magnifying glass – computer criminality concept. Image by Jirsak, iStockphoto.
The post The global data privacy power struggle appeared first on OUPblog.

 Over the past few weeks there have been several news stories about the ways in which mobile device apps can, and do, infringe on the privacy of users. The news pretty much broke when it was discovered that the social app, Path, was copying user address books without notifying users of that. Since the Path news came to light, people have discovered that that app was, and is, not the only app copying user information without notice.
Over the past few weeks there have been several news stories about the ways in which mobile device apps can, and do, infringe on the privacy of users. The news pretty much broke when it was discovered that the social app, Path, was copying user address books without notifying users of that. Since the Path news came to light, people have discovered that that app was, and is, not the only app copying user information without notice.
As the Washington Post noted in their article on the FTC report regarding privacy, apps, and children the landscape in the area of apps and privacy is something like the digital wild west. It’s all new territory and developers and users are learning what works and doesn’t work and how to marry safety and privacy with business. Many of us are now at least a bit savvy about user privacy in a web-based social media world. A world in which Facebook changes its privacy features on what seems like a weekly basis and Google is making changes to their privacy policy on March 1. Now is the time to become savvy about privacy in a mobile device/app world and to have conversations with teens about how they stay safe in these environments. A good way to get started is to:
-
Read the articles linked above to become familiar with the issues and also take a look at this short slideshow, from Larry Magid of SafeKids.com, about ways to make sure your privacy is protected in the app world.
- Start talking with teens about the apps they use and how they can guarantee that when they use them their privacy is protected. Brainstorm ways that they can check-out how an app does and doesn’t use personal information. Perhaps setup a project in which teens do some research in order to find out what apps have the best privacy track record and which are lacking.
- Become familiar with apps. If you haven’t used apps on a smartphone or tablet make sure you spend some time doing just that. Ask friends, teens, or colleagues if you can take a look on their devices if you don’t have one yourself. The only way to really be informed is to have some first-hand experience. A great way to find out what apps are worth checking out is via the YALSA App of the Week column on this blog.
- Don’t assume that because of these breaches that all apps are bad and people should just stop using them. That’s not true, all apps aren’t bad. And, people aren’t just going to stop using them. Apps provide a great deal of useful tools and information to children, teens, and adults. We all just have to get really smart about what’s going on behind the scenes. In his New York Times article Nick Bilton gets to this point very well when he states, “The argument that if consumers care about their privacy they shouldn’t use these technologies is a cop-out. This technology is now completely woven into every part of society and business. We didn’t tell people who wanted safer cars simply not to drive. We made safer cars.”
Now is the time to gain the skills and

[Kindle image by Tim Spalding, thanks Tim!]
I went to a staff meeting on Friday at the local library where I sometimes work. We did some strategic planning, some walking around the building looking at stuff that could be improved, and some “how to download various digital media format” exercises. We use Overdrive via Listen Up Vermont which gives us access to audiobooks and ebooks in EPUB and Kindle formats. I’m pretty okay at this sort of thing so we clicked around and saw how stuff worked and had a few little glitches but basically stuff was okay. I’ve been following the Amazon book lending story through the blogs the past few weeks and I’ve been skeptical but more curious than anything. I don’t have a Kindle but I’ve seen how popular they are and I was curious how this would all work. Well, as some bloggers have pointed out, it sort of doesn’t. Or, rather, it seems to require compromises to our systems and more importantly to our professional values. I’m hoping these issues can be resolved, but honestly if we can’t lend with some modicum of patron privacy, we shouldn’t be lending.
This is all leading up to an email exchange I had with a reader who was wondering the best way to raise concerns with his librarian about the user experience of borrowing a Kindle book from his library to use with the Kindle app on a non-Kindle device. Apparently, while the process to obtain the book wasn’t too difficult, the process to actually get RID of the book once returned [without a lot of pesky "hey maybe you should BUY this" cajoling] was actually fairly difficult. The default settings are, not surprisingly, strongly urging that the patron purchase (not renewal, not some sort of overdue notification) the book that they have just “returned.” I’ll let the patron speak for himself on this process. His name is Dan Smith and this is reprinted with his express permission.
______
My first experience at “borrowing a Kindle book from the library” has left me with a bad taste in my mouth. It did not feel like borrowing a book from a library. It felt like a salesperson had sold me a book with a “no-risk free home trial” and was pestering me to buy it at the end of the trial period.
I feel that Amazon’s commercial promotion is excessive, and imposes inappropriately on public library patrons. Would you allow distributor’s rep to stand in the hall, grabbing people on their way to the return slot, saying “Stop! Why RETURN it when you can BUY it instantly for just $12.95?”
Yes, some of the irritations can be sidestepped, and as a savvy user I now know how. But Amazon took advantage of my innocence.
FIrst, the book was all marked up! Dotted underlines here and there on almost every page. It was like taking out a library book and finding someone had gone over it with a highlighter! Amazon allow “library” ebooks to be marked and annotated. Instead of cleaning them up for the next patron, it leaves them in place, and encourages you make your own marks for other people to see. I thought this was just some misguided idea about social networking, but it’s more sinister than that.
I turns out that there is a global setting, “Popular Highlights,” which controls whether you see these marks. B

By: Kirsty,
on 6/22/2011
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
injunction,
Editor's Picks,
*Featured,
Law & Politics,
fair hearing,
gagging order,
john hemming,
king canute,
mark warby,
privacy law,
super-injunctions,
canute,
tugendhat,
gagging,
injunctions,
hemming,
Current Events,
privacy,
twitter,
glossary,
Courts,
Add a tag
By Mark Warby
My mum told me the other day that she found all this publicity about privacy, super-injunctions, and Twitter most confusing. So do I, because the way it is reported seems to bear little resemblance to the world I thought I worked in and knew. So in case anybody else out there is befuddled I thought I would have a go at clarifying things by providing a glossary. Here are some of the key terms, and some definitions. In some cases I have offered alternatives, to help understanding.
A bit of cross-referencing is necessary here, so I have used asterisks to mark out terms you will find explained elsewhere in the glossary.
Privacy law glossary
Apply to the court: (1) what a person has to do if they want to obtain an injunction* (2) what any person has a right to do if served with or notified of an injunction* with which they disagree, and want to challenge (3) an expensive and uncertain alternative to Contempt of Court no 2* (4) see Waste of time and money.
Appeal: (1) what any person can seek to do if a court makes an order that affects them with which they disagree (2) see Apply to the Court no 3 (3) see Apply to the Court no 4.
Contempt of court: (1) speech or act which defies an order of the court, or defeats or undermines its purpose (2) see Making a Mockery.*
Court of Appeal: (1) one of the Houses of Parliament (2) Twitter (3) place staffed by Judges* to which you can go to obtain a fair hearing and challenge an injunction you disagree with (4) see Apply to the court nos 3 and 4.
Democracy: system of government using. See Votes.*
Fair hearing: (1) a fundamental human right (2) what people go to a court to get, when asserting their rights (3) reading Twitter, not consulting the people affected, deciding unilaterally what is right or wrong, and announcing it to the world.
Freedom of expression: (1) unequivocally good thing in all possible circumstances, when exercised by the print media or online (2) one fundamental right which may come into conflict with another, namely privacy*, so that a delicate balance has to be struck.
Gagging order: bad thing; order of a Judge that prohibits something being said that ought to be made known.
Hemming: fearless campaigner for the freedom to use parliamentary privilege to name with impunity well-known people who have obtained injunctions* from Judges* to prevent disclosure of information in the public interest* (2) not.
Injunction: (1) court order which prohibits things being said or done which the court considers ought not to happen (2) gagging order* made by a Judge.*
Issuing: (1) what celebrities do with injunctions, apparently (2) the act of starting legal proceedings, preliminary to asking a court to rule on a claim.
Judge: (1) person who makes it up as they go along, treats freedom of speech with contempt (2) fantasist with delusions of omnipotence (see also Unelected*) (3) individual appointed by the state to decide disputes about legal rights after a fair hearing.*
King Canute: see Judge no 2*. See also next section.
Making a mockery: (1) an exercise of freedom of speech* on Twitter or otherwise which involves deliberately disobeying a court order, undermining its effect, and so demonstrating Judges to be King Canute* (2) see Contempt of Court.*
Parliamentary privilege: fundamental right of any MP to do with impunity an act which would be a contempt of court*.
Privacy rights: (1) bad thing; synonym for adulterous
The ACLU has made a useful post talking about the Department of Justice’s released statistics about their surveillance activities. Surveillance is up. Section 215 is sunsetting. Osama is dead. What now?
The government more than quadrupled its use of secret court subpoenas, known as 215 orders, which give the government access to “any tangible thing,” including a wide range of sensitive information such as financial records, medical records, and even library records. In 2010, the FBI made 96 applications, up from just 21 in 2009.

I’ve been reading with interest the news stories lately about Epsilon. For those of you who don’t know Epsilon is a company that does marketing. Many companies give Epsilon customer lists and Epsilon uses that information to, say, email you about the latest Hilton Honors promotions. Except that there was a data breach and Epsilon lost up to 250 million email addresses
along with information such as who those people were customers of. So, for example, they’d have my email address and the knowledge that I was a Hilton Honors member. So, a lot of people got emails in the last mont from companies saying “Um, be especially on the lookout for phishing attacks” and a lot of people were asking “Why did Epsilon have my email address in the first place, didn’t I sign a privacy policy with Company X?” And the answer is complicated. When you let Hilton Honors use your information to send you marketing information you are, in a way, letting them give the email address to marketing companies.
The reason I care about this at all is two reasons. One, there is a useful analog with libraries and how they handle their email lists of patrons. Obviously patron data is private and comes under whatever privacy laws a state has and whatever policies the library has. But is a library allowed to market to patrons? Or give these lists to peopl to market on the library’s behalf? This was the concern when the public library in Dixon California emailed patrons to let them know about ongoing library renovation plans and asked them to consider making donations. People who are not pleased with the library renovations, the Dixon Carnegie Library Preservation Society, is arguing that the librarian acted improperly when they gave patron email addresses to a consulting company without patron consent. Now let me just state I pretty well side with the library on this one, but it’s sure to be an increasingly contentious topic as libraries have more and more diffrent kinds of patron data to keep private.
And the second reson is just a cautionary tale. Many people with iphones are aware by now that the phone tracks where you go. I mean it has to in order to be a phone, but it stores this data in unencrypted form on both the phone and the synced compueter, forever. This means that anyone with access to a simple open source tool such as this one can make lovely maps like the one above. Good to know, and good to understand. As libraries move more towards mobile applications and mobile awareness generally, understanding how this sort of data works will be an important part of making sure we know how, when and why to keep it private.
In the last week, two blog posts that I've commented on have found themselves in The Guardian. One was Lucy Coats' trenchant post on ABBA about A Certain Person and his unpleasant brain injury comment. The other was independent bookseller Vanessa Robertson's equally trenchant piece about World Book Night. I’m interested in what happened to them and the appended comments and in what this means for all of us.
After Vanessa's WBN post, I'd left a comment, among many comments from other people, and mine was picked up by a journalist and quoted (well, half of it) in her subsequent Guardian piece. No other comment was quoted by name. In the Guardian, my quote was prefaced by the statement, "Author Nicola Morgan was among those happy to air objections..." This implied that I'd been asked by the journalist. Actually, she had tried to contact me but my phone was off while I was doing school talks and by the time I got her message it was too late: her deadline had passed. One might think that because I’d commented, I was de facto “happy”. Well, yes: I was happy to comment amongst all the other commenters but the small but important difference now was that my comment had appeared on another forum, in print, with another headline, and taken out of its original discussion. It had been, in effect, re-contextualised by someone else. I am not annoyed, because I utterly stand by what I said, and the journalist's piece was good. But it got me thinking.
In Lucy's post, one commenter's remark was also taken and used in the Guardian piece on that subject, and later, on ABBA, that commenter expressed a similar surprise to mine. I’m not criticising journalists, by the way. There may be an issue of asking permission but I’m not interested in that just now. Ditto any copyright issues to do with quoting from blogs.
So what am I saying? I am saying that the internet has changed something about conversation. Blogs, unless actually private and hidden, are public, and when we comment, although it might feel like a discussion where we're all in the room, we are putting our views out there in a very public way. We cannot then control where our comments will appear. And it's permanent. The internet doesn’t forget. The internet has blurred the once clear divide between the spoken word and the printed word. It's more permanent than either and possibly more powerful.
In a good old offline conversation, you know who is there, who is listening - unless you are being bugged - and you know it is unlikely your words will find themselves discussed in public elsewhere. You can make mistakes, change your mind, clarify what you mean if someone doesn't understand. No one can take your words out of context because all those in the discussion know the context. The discussion is also moderated by those in it. It is controlled and yet can be wild and free ranging. There is little at stake other than the opinions of those present.
In an online conversation, the new conversation, all that is different. There is much more at stake, much more that can go wrong, much less control. You don't know who's listening and you don't know what will happen to your words, except for one thing: they will remain.
We also need to realise that Facebook and Twitter conversations are now watched by journalists. You make comments on Facebook and those comments can be quoted or passed on to people outside your FB circle. I have heard of people having to "defriend" others because they are worried that those people, not being actual friends, may use their comments against them. And I worry about the unguarded comments that some people make on Facebook, because FB sometimes feels like a party, with a
I read a discussion forum today about an author's struggle with privacy. We're not talking, "Hey I want to hide from my fans" but more of "Why are you showing up on my doorstep and how do you know where I live?".
For years we write. We query.We get rejected, defeated, and heartbroken because we haven't found an agent or publisher. We keep our eyes on the prize though. A gorgeous, solid, hardback book with a stunning, artistic cover and our name written in bold letters. Finally an author's Holy Grail has been achieved.
But now what? Hopefully, you'll sell the book, gather a few fans here and there. During this euphoric time in your life, the googling will start. People that love your work want to know more about YOU. So they search and with an overload of cyber information at their disposal, it should be easy to find out everything from your favorite meal to where your children go to school.
It's a scary, scary thought. Hell, it's scary even if your not famous. Stalking occurs for a variety of reasons and not just to famous people.
It's important to be savy now, before you get 'The Call' and before you're on the NYTimes bestseller list.
Some of the suggestions were:
*Have your personal information removed from spokeo.com
*Use a PO Box or have all fan mail come through your publisher
*Have an unlisted phone number
*Have multiple phone numbers. One for personal use and one you can give out and change easily if you need to.
*Have multiple e-mail addresss. One for personal relationships, another for fans, journalists, etc
*Don't post information or pictures of your children on the web
*Use a Facebook Fan Page rather than a personal page
*Have all your Facebook setting set to friends and family only
*Don't link to your family on Facebook and review your privacy settings or turn some information off like the city you live in
*Have home security
*When asked where you live for book jackets, press release, etc. give a vague geographic location or state like MidWest, Texas, New England
With all the info out there, it's important to protect our privacy and loved ones now and not wait until our name appears on a book cover.
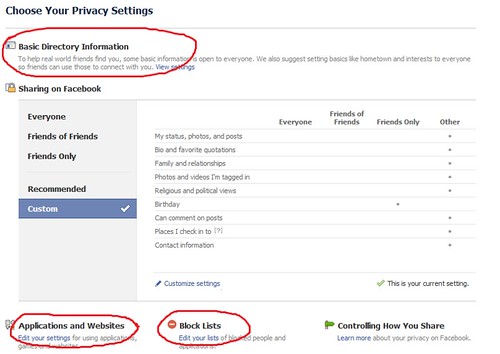
Privacy settings on Facebook are important and I cannot stress this enough. No matter whether it’s for games or work or marketing, setting your privacy right can avoid some embarrassing moments and data/identity theft.
Facebook by default sets all Privacy Settings to Public. i.e. viewable by everyone. That means, if you have never visited your Privacy Setting page and customised it, anyone and everyone in the world can see all your information. If you’re someone who has no data on Facebook then great, don’t worry about it! But, if you have personal data, you better get cracking on customising it.
So how do you set your privacy right?
- Click on the ‘Account’ tab on the right-top-corner of the page.
- Choose and click on ‘Privacy Settings’
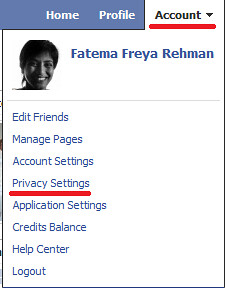
- Choose Your Privacy Settings. Spend some time on this page checking through your information. It’ll definitely be worth your time.
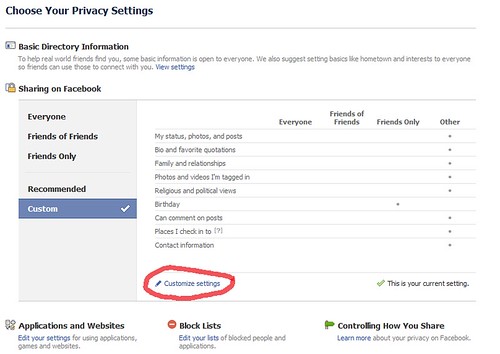
Click on ‘Customise settings’ to control who views your posts or shares. If you have created ‘Lists’ for your friends, doing this would be easier. Read my article Creating Lists on Facebook for more on Lists.
- This page has three main sections – Things I share, Things others share, Contact Information. Click on the drop down next to each sub-section and select the ‘Custom’ option.
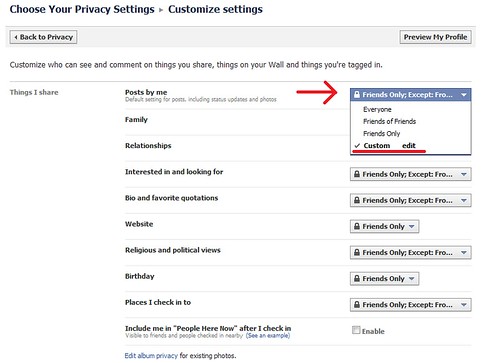
- In the pop-up that appears you can select who should see this type of data and who shouldn’t. You can also specify certain people by name or by list.
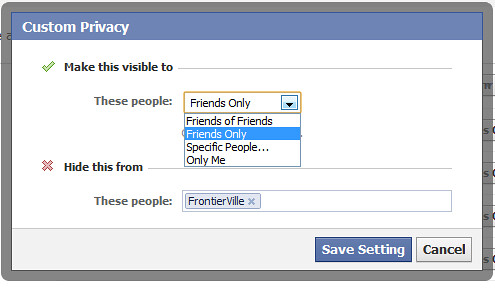 If you play games on Facebook, remember to add your ‘game list’ in the ‘Hide this from’ section for all sub-sections so your data is safe from gamers and strangers.
If you play games on Facebook, remember to add your ‘game list’ in the ‘Hide this from’ section for all sub-sections so your data is safe from gamers and strangers.
- Set-up your custom settings for all the sub-sections.
- Once you’re done. Click on the ‘Preview My Profile’ button (towards the top of the page) and check to see what information is visible and if you are comfortable with the world seeing that.
- It is a good idea to go through the settings for the following on your privacy page too -
Basic Directory Information
Applications and Websites
Block Lists
Yesterday Twitter (and the web in general) was abuzz with news and reports related to technology, and in particular young people and technology. Was all the news worth paying attention to? Was all the news care-worthy? Here are some thoughts:
Care: Reputation Management and Social Media
The Pew Internet in American Life Project released a report about reputation management and social media. The focus of the report is on how people, of all ages, manage what others know about them through social network environments.
 A key finding in the Pew study is that young adults – defined in this instance as 18 to 29 – are very likely to change their privacy settings within social media environments. This age group, more than older users of social media, do know the impact that the information they make available online has on their reputation. While this doesn’t mean that we as librarians and educators don’t need to educate young people about privacy implications of what they post online, it does suggest that conversations with teens about online privacy need to be framed not around “you need to be private” with an assumption that young people don’t know that already, but instead focus on, “here’s how to be private” with an understanding that making decisions about and knowing how to use privacy settings in social networks affectively might be difficult.
A key finding in the Pew study is that young adults – defined in this instance as 18 to 29 – are very likely to change their privacy settings within social media environments. This age group, more than older users of social media, do know the impact that the information they make available online has on their reputation. While this doesn’t mean that we as librarians and educators don’t need to educate young people about privacy implications of what they post online, it does suggest that conversations with teens about online privacy need to be framed not around “you need to be private” with an assumption that young people don’t know that already, but instead focus on, “here’s how to be private” with an understanding that making decisions about and knowing how to use privacy settings in social networks affectively might be difficult.
The implications section of the Pew report includes this text:
“Young adults, perhaps out of necessity, are much more active curators of their online identities when compared with older adults. When they change privacy settings, delete tags and comments, and request that information about them be removed, they are demonstrating a desire to exert control over the content they share and the tide of information that others post about them online. However, certain privacy controls on social media sites have become increasingly difficult to navigate. These changes, instituted after the data for this report was gathered, raise questions about the efficacy of users’ current efforts to restrict access to the information posted to their profiles.”
And that leads me to
Care: Facebook Updates Privacy Settings – Again
For the past several weeks, Facebook has been in the news as the result of new services added to the social network. The new services are supposed to give users a better experience, however the launch of these services once again complicated the privacy settings on Facebook, they were pretty complicated already, and caused many to question what Facebook was up to.
Because of the dissatisfaction of users with the privacy implications of the most recent Facebook update, Mark Zuckerberg, the founder and CEO of the company, announced yesterday that the privacy settings on the site would be simplified.
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting3-150x150.jpeg)
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting2-150x150.jpeg)
![[cross-writing]](http://www.asideofbooks.com/wp-content/uploads/2016/05/Victoriancrosswriting1-150x150.jpeg)







 Data protection law has traditionally been viewed as a dreary subject of interest only to a few specialists. But whether it involves filling out government forms, purchasing items on the web, communicating with friends and relatives online, or checking in for a flight, almost every activity we engage in nowadays involves the processing of personal data. The growing importance of data processing is reflected in the large number of countries (approximately 100) around the world that have enacted data protection laws, and the countries and international organisations (including the
Data protection law has traditionally been viewed as a dreary subject of interest only to a few specialists. But whether it involves filling out government forms, purchasing items on the web, communicating with friends and relatives online, or checking in for a flight, almost every activity we engage in nowadays involves the processing of personal data. The growing importance of data processing is reflected in the large number of countries (approximately 100) around the world that have enacted data protection laws, and the countries and international organisations (including the  Dr. Christopher Kuner is editor-in-chief of the journal
Dr. Christopher Kuner is editor-in-chief of the journal  Over the past few weeks there have been several news stories about the ways in which mobile device apps can, and do, infringe on the privacy of users. The news pretty much broke when it was discovered that the social app,
Over the past few weeks there have been several news stories about the ways in which mobile device apps can, and do, infringe on the privacy of users. The news pretty much broke when it was discovered that the social app, 










Hmmm, surveillance, huh? What would they want with my small scribblings? Makes you wonder what they are doing with all those gazillion bits of data.
I’m excited to hear that SSL will be standard on wordpress.com subdomains soon. I really don’t like the idea that anyone’s spying on me, especially when I’m not doing anything wrong.
Thanks, WordPress!
This is great! Thank you. BTW, if you added a feature where users can pay to get SSL certs for their custom domain hosted by WordPress.com, I’d for one would gladly pay. Wink, wink, nudge, nudge…
Stand now.
I support this!
Reblogged this on A View from the Grid and commented:
Passivity is acceptance.
He who rules the net rules the world! We have become internet slaves and I am not sure we can ever be truly free from censorship but of course I support and appreciate the efforts of Automatic in fighting this sinister intrusion and violation of privacy!
My wife and I have discussed this many times. While we don’t believe the federal government has any business snooping about as they do in the name of national security, we don’t frankly care if they snoop us.
They would be bored to death with our internet activities. There is nothing to be hidden of our internet use.
We believe that those who fear this intrusion most are those whom have things to hide in the shadows. Our internet activities are all in the light. Clearly, Washington is misusing and abusing technology.
Excellent! This is great news and I support WordPress in its efforts to protect its members.
Thank you. It is disturbing the lengths governments go and spin it as being to protect their people. They’re just snooping. I’m all for RESETTING THE NET.
Thank you for participating in Re-Set the Net!
“All that is necessary for evil to triumph is for good men to do nothing.” Edmund Burke
You’d think humanity would have learned this lesson by now.
Great news, just hoping it won’t slow down the servers significantly
LOVE this, and THANK YOU.
Excellent, this is good to hear.
Much needed, and thanks.
Who in their right mind would post something on a public forum that they know the government would be interested in? Nevermind….evidently more than I thought.