new posts in all blogs
Viewing: Blog Posts Tagged with: internet, Most Recent at Top [Help]
Results 26 - 50 of 347
How to use this Page
You are viewing the most recent posts tagged with the words: internet in the JacketFlap blog reader. What is a tag? Think of a tag as a keyword or category label. Tags can both help you find posts on JacketFlap.com as well as provide an easy way for you to "remember" and classify posts for later recall. Try adding a tag yourself by clicking "Add a tag" below a post's header. Scroll down through the list of Recent Posts in the left column and click on a post title that sounds interesting. You can view all posts from a specific blog by clicking the Blog name in the right column, or you can click a 'More Posts from this Blog' link in any individual post.

By: Elizabeth Gorney,
on 8/8/2014
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
adolescent psychology,
Daniel Romer,
romer,
prot,
harms,
teens,
Books,
internet,
gaming,
video games,
Media,
youth,
violence,
xbox,
adolescents,
addiction,
APA,
new media,
old media,
media psychology,
*Featured,
American Psychological Association,
Science & Medicine,
Psychology & Neuroscience,
APA2014,
Add a tag
By Daniel Romer
Now that the Internet has been with us for over 25 years, what are we to make of all the concerns about how this new medium is affecting us, especially the young digital natives who know more about how to maneuver in this space than most adults?
Although it is true that various novel media platforms have invaded households in the United States, many researchers still focus on the harms that the “old” media of television and movies still have on youth. The effects of advertising on promoting the obesity epidemic highlight how so much of those messages are directed to children and adolescents. Jennifer Harris noted that children ages 2 to 11 get nearly 13 food and beverage ads every day while watching TV, and adolescents get even more. Needless to say, many of these ads promote high-calorie, low-nutrition foods. Beer is still heavily promoted on TV with little concern about who is watching, and sexual messages are rampant across both TV and movie screens. None of this is new, but the fact that these influences remain so dominant today despite the powerful presence of new media is testament enough that “the more things change, the more they stay the same.”
When it comes to the new media, researchers are more balanced. Sonia Livingston from the UK reported on a massive study done in Europe that found a lot of variation in how countries are dealing with the potential harms on children. But when all was said and done, she concluded that the risks there were no more prevalent than those that kids have confronted in their daily lives offline. What has changed there is the talk about the “risks,” without much delving into whether those risks actually materialize into harms. Many kids are exposed to hurtful content in this new digital space, but many also learned how to cope with them.

2013 E3 – XBOX ONE Killer Instinct B. Uploaded by – EMR -. CC-BY-2.0 via Flickr.
The perhaps most contentious of the new media influences is the emergence of video gaming, either via the Internet or on home consoles. The new DSM-5, which identifies mental disorders for psychiatrists, suggests that these gaming activities can become addictive. Research summarized by Sara Prot and colleagues suggests that about 8% of young people exhibit symptoms of this potential disorder. At the same time, we still don’t know whether gaming leads to the symptoms or is just a manifestation of other problems that would emerge anyway.
Aside from the potential addictive properties of video games, there is considerable concern about games that invite players to shoot and destroy imaginary attackers. Many young men play these violent video games and some of them are actually used by the military to prepare soldiers for battle. One could imagine that a young man with intense resentment toward others could see these games as a release or even worse as practice for potential harmdoing. The rise in school shootings in recent years only adds to the concern. The research reviewed by Prot is quite clear that playing the games can increase aggressive thoughts and behavior in laboratory settings. What remains contentious is how much influence this has on actual violence outside the lab.
On the positive side, other researchers have noted how much good both the old and new media can provide to educators and to health promoters. It is helpful to keep in mind that many of the concerns about the new media may merely reflect the age old wariness that adults have displayed regarding the role of media in their children’s behavior. In a recent review of the effects of Internet use on the brain, Kathryn Mills of University College London pointed out that even Socrates was skeptical of children learning to write because it would reduce their need to develop memory skills. Here again, the more things change, the more they remain the same.
Daniel Romer is the Director of the Adolescent Communication and Health Institutes of the Annenberg Public Policy Center. He directs research on the social and cognitive development of adolescents with particular focus on the promotion of mental and behavioral health. His research is currently funded by the National Cancer Institute and the National Institute on Drug Abuse. He regularly serves on review panels for NIH and NSF and consults on federal panels regarding media guidelines for coverage of adolescent mental health problems, such as suicide and bullying. He is the author of Media and the Well-Being of Children and Adolescents.

Subscribe to the OUPblog via email or RSS.
Subscribe to only psychology articles on the OUPblog via email or RSS.
The post Youth and the new media: what next? appeared first on OUPblog.


By: Daniella Frangione,
on 8/7/2014
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Tim Berners-Lee,
otlet’s,
otlet,
Books,
History,
Biography,
Technology,
*Featured,
Science & Medicine,
internet,
science,
q&a,
Electronics,
invention,
World Wide Web,
Alex Wright,
Birth of the Information Age,
Cataloging the World,
Paul Otlet,
Add a tag
As soon as humanity began its quest for knowledge, people have also attempted to organize that knowledge. From the invention of writing to the abacus, from medieval manuscripts to modern paperbacks, from microfiche to the Internet, our attempt to understand the world — and catalog it in an orderly fashion with dictionaries, encyclopedias, libraries, and databases — has evolved with new technologies. One man on the quest for order was innovator, idealist, and scientist Paul Otlet, who is the subject of the new book Cataloging the World. We spoke to author Alex Wright about his research process, Paul Otlet’s foresight into the future of global information networks, and Otlet’s place in the history of science and technology.
What most surprised you when researching Paul Otlet?
Paul Otlet was a source of continual surprise to me. I went into this project with a decent understanding of his achievements as an information scientist (or “documentalist,” as he would have said), but I didn’t fully grasp the full scope of his ambitions. For example, his commitment to progressive social causes, his involvement in the creation of the League of Nations, or his decades-long dream of building a vast World City to serve as the political and intellectual hub of a new post-national world order. His ambitions went well beyond the problem of organizing information. Ultimately, he dreamed of reorganizing the entire world.
What misconceptions exist regarding Paul Otlet and the story of the creation of the World Wide Web itself?
It’s temptingly easy to overstate Otlet’s importance. Despite his remarkable foresight about the possibilities of networks, he did not “invent” the World Wide Web. That credit rightly goes to Tim Berners-Lee and his partner (another oft-overlooked Belgian) Robert Cailliau. While Otlet’s most visionary work describes a global network of “electric telescopes” displaying text, graphics, audio, and video files retrieved from all over the world, he never actually built such a system. Nor did the framework he proposed involve any form of machine computation. Nonetheless, Otlet’s ideas anticipated the eventual development of hypertext information retrieval systems. And while there is no direct paper trail linking him to the acknowledged forebears of the Web (like Vannevar Bush, Douglas Engelbart, and Ted Nelson), there is tantalizing circumstantial evidence that Otlet’s ideas were clearly “in the air” and influencing an increasingly public dialogue about the problem of information overload – the same cultural petri dish in which the post-war Anglo-American vision of a global information network began to emerge.
What was the most challenging part of your research?
The sheer size of Otlet’s archives–over 1,000 boxes of papers, journals, and rough notes, much of it handwritten and difficult to decipher–presented a formidable challenge in trying to determine where to focus my research efforts. Fortunately the staff of the Mundaneum in Mons, Belgium, supported me every step of the way, helping me wade through the material and directing my attention towards his most salient work. Otlet’s adolescent diaries posed a particularly thorny challenge. On the one hand they offer a fascinating portrait of a bright but tormented teenager who by age 15 was already dreaming of organizing the world’s information. But his handwriting is all but illegible for long stretches. Even an accomplished French translator like my dear friend (and fellow Oxford author) Mary Ann Caws, struggled to help me decipher his nineteenth-century Wallonian adolescent chicken scratch. Chapter Two wouldn’t have been the same without her!

Photograph of Paul Otlet, circa 1939. Reproduced with permission of the Mundaneum, Mons, Belgium.
How do you hope this new knowledge of Otlet will influence the ways in which people view the Internet and information sites like Wikipedia?
I hope that it can cast at least a sliver of fresh light on our understanding of the evolution of networked information spaces. For all its similarities to the web, Otlet’s vision differed dramatically in several key respects, and points to several provocative roads not taken. Most importantly, he envisioned his web as a highly structured environment, with a complex semantic markup called the Universal Decimal Classification. An Otletian version of Wikipedia would almost certainly involve a more hierarchical and interlinked presentation of concepts (as opposed to the flat and relatively shallow structure of the current Wikipedia). Otlet’s work offers us something much more akin in spirit to the Semantic Web or Linked Data initiative: a powerful, tightly controlled system intended to help people make sense of complex information spaces.
Can you explain more about Otlet’s idea of “electronic telescopes” – whether they were feasible/possible, and to what extent they led to the creation of networks (as opposed to foreshadowing them)?
One early reviewer of the manuscript took issue with my characterization of Otlet’s “electric telescopes” as a kind of computer, but I’ll stand by that characterization. While the device he described may not fit the dictionary definition of a computer as a “programmable electronic device” – Otlet never wrote about programming per se – I would take the Wittgensteinian position that a word is defined by its use. By that standard, Otlet’s “electric telescope” constitutes what most of us would likely describe as a computer: a connected device for retrieving information over a network. As to whether it was technically feasible – that’s a trickier question. Otlet certainly never built one, but he was writing at a time when the television was first starting to look like a viable technology. Couple that with the emergence of radio, telephone, and telegraphs – not to mention new storage technologies like microfilm and even rudimentary fax machines – and the notion of an electric telescope may not seem so far-fetched after all.
What sorts of innovations would might have emerged from the Mundaneum – the institution at the center of Otlet’s “World City” – had it not been destroyed by the Nazis?
While the Nazi invasion signalled the death knell for Otlet’s project, it’s worth noting that the Belgian government had largely withdrawn its support a few years earlier. By 1940 many people already saw Otlet as a relic of another time, an old man harboring implausible dreams of international peace and Universal Truth. But Otlet and a smaller but committed team of staff soldiered on, undeterred, cataloging the vast collection that remained intact behind closed doors in Brussels’ Parc du Cinquantenaire. When the Nazis came, they cleared out the contents of the Palais Mondial, destroying over 70 tons worth of material, and making room for an exhibition of Third Reich art. Otlet’s productive career effectively came to an end, and he died a few years later in 1944.
It’s impossible to say quite how things might have turned out differently. But one notable difference between Otlet’s web and today’s version is the near-total absence of private enterprise – a vision that stands in stark contrast to today’s Internet, dominated as it is by a handful of powerful corporations.
Otlet’s Brussels headquarters stood almost right across the street from the present-day office of another outfit trying to organize and catalog the world’s information: Google.
Alex Wright is a professor of interaction design at the School of Visual Arts and a regular contributor to The New York Times. He is the author of Cataloging the World: Paul Otlet and the Birth of the Information Age and Glut: Mastering Information through the Ages.
Subscribe to the OUPblog via email or RSS.
Subscribe to only technology articles on the OUPblog via email or RSS.
The post Paul Otlet, Google, Wikipedia, and cataloging the world appeared first on OUPblog.

By: Mark Myers,
on 8/5/2014
Blog:
(
Login to Add to MyJacketFlap)
JacketFlap tags:
children,
Relationships,
internet,
technology,
humor,
tech,
teenagers,
parenting,
Men,
wifi,
funny,
Dad,
husband,
isp,
It Made Me Laugh,
Add a tag
The wifi in my eldest daughter’s laptop died recently. Being the home’s Chief Technology Officer, I worked through the handy troubleshoot on the system which told me it was working perfectly. Of course, the inability to connect to the internet and the distraught look on my poor daughter’s face told me it wasn’t. No worries, I bought a USB dongle and she was up and running.
Little did I know that my trouble-shooting skills would soon be needed again. A week ago, she informed me that her dongle wasn’t working. Of course, at 11:15, my system was shut down, so I didn’t pay much attention and went to bed. When I awoke, I realized it wasn’t her computer – there was a wholesale internet outage in the house!
I think that is mentioned in Revelation, isn’t it? The Mark of the Beast and the inability to access High-Speed Wireless is in chapter 13, if I remember correctly. I looked outside and it didn’t appear the Battle of Armageddon had begun yet. A check of the beds told me the wife and kids were still here, so the rapture hadn’t left me behind (Whew!)
But I still had no internet.
This has happened before and I fixed it. What did I do? Oh yeah, I unplugged it and it rebooted itself. So I pulled the plug and let it regenerate. Unfortunately, the light blinking was still red long after power was restored. So I called my ever-helpful internet service provider and got stuck in the web of automated attendants who sound helpful, but are very patronizing. Don’t they know I am the CTO? That should give me some status, I would think.
My biggest problem wasn’t the self-righteous know-it-all computer voice on the other end of the phone, it was the fact that my cell phone service is spotty in the basement where the router resides. So I put the phone on speaker and listened as best I could. Like a rat pushing through a maze, I found the tech support cheese after seventeen minutes and the new, smarter sounding Tech Support Weenie voice tells me we are going to have to restart the system.
TSW: I will now tell you how to restart your system. This is a medium level procedure and will take approximately 3-5 minutes.
Okay
TSW: Can you see your internet router?
Yes
TSW: Please find the power cable on the back of the router and say yes when you’ve found it.
Got it
TSW: I didn’t understand you.
Er… Yes
TSW: Trace the cable to the electric outlet. Unplug the cable and wait 10 seconds before plugging it back in.
Well, that’s what I did before, but okay
TSW: Did this solve your problem?
NO!
At that point, my spotty cell service affected my ability to clearly hear the next steps in the process. What I am pretty sure it said was for me to disconnect all cables, kick the box across the room, plug it back in and see if any lights were blinking. Repeat until no lights function.
Done!
After I hung up, I went to work early and left this note on the floor:

The good news, there is free wifi at the hotel, but I really wish they would call.
Filed under:
It Made Me Laugh 


By: Kathy Temean,
on 8/4/2014
Blog:
Writing and Illustrating
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Tips,
Internet,
Advice,
Process,
article,
authors and illustrators,
Publishing Industry,
Marketing a book,
How to Sell More Books,
Amazon Look Inside,
Amazon Strategies,
How to Sell More Books Workshop,
Add a tag


Let’s take a look at another feature that Amazon offers anyone who sells their books on their site.
Don’t miss out on using this feature. This is another reason why it is important to make sure your first chapter sings.
Personally for me to buy, I look over five things:
Price: I buy lots of ebooks that are offered at $1.99 or less, without having read anything about them.
Cover: I don’t buy books where I don’t like the cover, unless someone else said they were good. I guess I believe in first impressions.
Reviews: I read what book is about and a couple reviews. A few bad reviews don’t stop me from buying, since I’ve read many top-seller books that I thought were great that received a few terrible reviews.
Publisher: I check out who published the book. If it is from a well-known publisher, that could seal the deal right there.
Look inside: If I have not clicked the button to buy, I will “Look inside”. That’s when I put on my editor/agent hat and only give five minutes to the author to grab me before I make my decision. Sometimes the problem is that the book really grabs you and then you have to read the whole thing, even when the desk is piled with work and the kitchen needs to be clean. Many of those books have been self-published, so don’t stick your nose up at them or else you might missed something really good.
Here are some tips on using the “Look inside” feature.
1. Keep front matter to a minimum. You want to make sure the reader can get to the meat of the story quickly. This is also important to do this with the full ebook.
2. Amazon Reviews. Work hard to get as many as you can when you launch the book. This will help raise your ranking and buyers who have read the first pages will look at this, especially if you are self-published.
3. At the end of your book you should ask the reader to write a review. Stats show that this helps you increase your sales numbers.
4. Hot New Releases List on Amazon should be in the forefront of your mind when planning a launch. Talk to your publisher to see if they have planned your novels launch based on other similar books coming out. If there are too many it will hurt your chances of making the list. The list is only good for the first 30 days of a books release.
5. Making sure your blog followers know about your book and doing book tours can help get the word out. It’s nice to get the buzz going, but you need to make sure you keep the big guns for the launch date.
Talk tomorrow,
Kathy
Filed under:
Advice,
article,
authors and illustrators,
Internet,
Marketing a book,
Process,
Publishing Industry,
Tips Tagged:
Amazon Look Inside,
Amazon Strategies,
How to Sell More Books,
How to Sell More Books Workshop 

I don't 'do' Snapchat, unlike my little sister (19 years old), but I love dreaming about the narrative possibilities it offers. A murder mystery, where the serial killer sends short Snapchat videos with clues every time s/he strikes...
 |
| yeah, the logo looks more like a Casper story |
Anyway, I'll never write that story, but I do love literature that talks about new technology. In many ways, it's difficult to think of a contemporary social realistic story, especially for teenagers, which wouldn't include smartphones and apps - Facebook, Tumblr, 2048, Google Maps - as a solution to many of the traditional adventure plotlines (nope, sorry, you can't be
actually lost; nope, sorry, you can't
actually be bored waiting for your train; nope, sorry, you couldn't
not have known that she was in a relationship (and it's complicated)).
But I like it even more when stories integrate technology in a non-gimmicky way - as an essential part of the plot, as the plot. Many such stories are realistic: it's impossible to keep track of stories that revolve around mystery blog-writers, from rom-coms to dramas. Others are supernatural, but even a fantastical story like
iBoy by Kevin Brooks is based on very real features of contemporary smartphones.
New technology offers possibilities both for entirely new plots and for interesting spins on older plots. There's been a spate of YA novels recently that revolve around revenge porn - one of them, in France, is mine. Of course revenge porn existed before smartphones, but the order of magnitude is different now, and so are, therefore, narrative possibilities - especially regarding character development, and some central themes of YA literature, such as gossip or bullying.
In my latest YA novel,
Comme des images, there are snippets of Facebook conversations, YouTube comments, texts, emails - breaking up the narrative from time to time. Those are
other voices, seemingly external to the plot, but actually crucial to it - because
the existence of those hundreds of other voices is the very reason why the central event is so important: it isn't just there, it's also commented on, in the whole world. Of course, you need to get those voices right, because it can just fail to ring true. Being friends on Facebook with teenagers of that age - in my case, my sister and all her friends - can help. I'm not sure I'd dare do it in English, where I'm not as familiar with the language used by teenagers.
So does being very active on these platforms, or at least having an excellent understanding of them. I cringe when I read books in which it is clear that the author (either by themselves or pushed by an editor) has attempted to include some (generally gimmicky) references to apps, software, video games or device without knowing anything about it (
"'I sent you a Twitter yesterday!' she chuckled.").
Hybrid texts where 'normal' narrative is sporadically broken by other types of discourse - from mock-tweets to mock-Wikipedia articles - can be highly sophisticated. There is immense value in harnessing the narrative possibilities that technological innovations offer us, not to be trendy; in part so that we continue to map, as faithfully as possible, the changes that are occurring in teenagers' lives, and make guesses as to how they might influence their personalities, their reactions, their tastes, their values. But it has literary and artistic value, too.
Such uses are not - or shouldn't be - just a way of spicing up a dull, ordinary story: they can be the opportunity for intensely original, groundbreaking advances in storytelling, for YA literature and beyond.
The only imperative is to avoid at all costs 'giving a message', 'warning' teenagers 'against' the 'dangers' of 'technology'.
But frustratingly, in order to make them palatable to mediators, this pedagogical 'guarantee' is frequently used to qualify works which should instead be praised for being uncomfortable or unsettling, both ideologically and linguistically. Let's keep the unease, at all costs. Personally, in my double life - virtual, real, barely separated - saturated with a myriad different voices and worldviews, I have no patience for consensus and all the time in the world for controversy.
______________________________________________________________________
Clementine Beauvais writes books in both French and English. The former are of all kinds and shapes, and the latter a humour/adventure detective series, the
Sesame Seade mysteries. She blogs
here about children's literature and academia and is on Twitter @
blueclementine.

By: Kathy Temean,
on 5/19/2014
Blog:
Writing and Illustrating
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Writing Tips,
Internet,
Technology,
Advice,
article,
authors and illustrators,
Jody Staton,
Writing: Goodgle Maps,
Tips,
Add a tag
Guest Blogger: Johanna Bilbo Staton
Map Program = Magic Carpet
You’re writing about a particular place, but your description feels flat. What you want, instead, is for your reader to feel as though they are actually “there.” Time for a field trip? But maybe that’s not possible—it would take time and money, lots of both if the location is far away from you.
I’ve discovered another solution: the map program on my computer and in particular the satellite and street level views. Granted, they will not give you the sounds and smells of a place, nor how it will look in a variety of seasons and weathers. Yet a map program can provide you with a surprisingly useful amount of detail.
Here are two examples of how I have used this resource:
Those computer maps are likely less than ten years old. How much use could they be for a story set almost five hundred years ago? Answer: quite a bit. Part of my story is set in Quarley, a tiny village of thatched-roof cottages in Hampshire, England. I know for a fact that they are at least forty years old. Four hundred plus? Maybe not. But in that relatively flat countryside there is one high spot, Quarley Hill, and it would have been there at the time of my story. I’ve seen it in person, but before that, I had seen it on Google Maps, and had written about it:
By mutual agreement, we angled toward Quarley Hill, a bump in the landscape that was our one local claim to any sort of height. Trotting up and down it, Frydd declared, was the best way for Bonesy to regain his mountain legs.
Later in the same manuscript, the main character and her companion are riding west toward Wales. Obviously there’s a big difference between modern roads in the UK and those of Tudor England. But I compared a British Ordnance Survey Historical Map of ancient Britain (also a useful resource) with a modern Ordnance Survey map of the same area, and so had a good idea of the probable route my riders took. Going to the area on Google Maps and going to the street view gave me this detail:
The Salisbury Plain had been flat. Now we rode through rolling countryside. We were in a valley, with slopes rising up on either side of the road.
Chances are I may find the program useful in a possible future project to be set in medieval Scotland—find a modern road through a wild area (plenty of those in the Highlands!) , and see what there is to see.
(However, Google seems to have changed its map program slightly since I did that. Instead of being able to move a little person-on-foot icon to a road, the program shows me a selection of street-level pictures. But this ought to be helpful also.)
I’ve also used the map program capabilities in my freelance copyediting, but in a way that would be just as useful for my writing. The text in question was from a contemporary novel set in New York City, in a scene that was set on the roof of a major theatrical landmark, and concerning what the characters could see from there. From the map program, I was able to determine which of the details given were, in fact, visible from that location, and which ones were iffy or impossible.
Writer’s block about your setting? Call up your map program, tell it where you want to go, let it get you down on the ground, and see what inspires you.
Filed under:
Advice,
article,
authors and illustrators,
Internet,
Technology,
Tips,
Writing Tips Tagged:
Jody Staton,
Writing: Goodgle Maps 

I, too, immediately thought, "Wow!" when I saw it.
I, too, accepted the idea that it must be David Foster Wallace's copy of
Ulysses, because, well ... you've heard of David Foster Wallace, right?
I'm teaching a course in literary analysis in the fall and so am collecting whatever images I can find of the ways (reasonable or absurd) that serious readers annotate what they read. I zoomed in on the image to see if I could figure out the logic (or illogic) of it. But the pages didn't look like
Ulysses to me. Nor, for that matter, did the style of annotation resemble what we know of DFW's style from
the books at the Ransom Center. I zoomed in, and though the resolution was quite low, I made out what seemed to be two names: Maureen O'Sullivan and, at the top, Robert Mitchum. It looked to me like a biography of Robert Mitchum.
It was easy enough to use Google Books to find a Robert Mitchum biography with this page layout:
Lee Server's Robert Mitchum: "Baby, I Don't Care".
I
sent a Tweet to the person who originally posted this; I assumed he'd just been joking, as anything with a bunch of weird annotations could jokingly be called DFW's something-or-other. Though I don't know his motivations, this still seems the most likely explanation. That everybody immediately and without any research assumed it was true and not a joke was ... illuminating.
I continued to wonder what the book was, though, and why someone had ... decorated it ... in the way they had. I didn't have time to track it down, but
Bibliokept did, and came up with some interesting stuff. Check out that link — it's a fun detective game.
The image is still compelling and fascinating, despite not being a book of DFW's nor a copy of
Ulysses. In some ways, it's more impressive that it
isn't a complex text like
Ulysses, but just a popular biography of a movie star.
What are the lessons here? 1.) Don't believe everything you see on the internet. 2.)
Sometimes things are even weirder than they seem at first.

By: Alice,
on 4/5/2014
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Law,
internet,
Technology,
Journals,
Current Affairs,
padlock,
*Featured,
international law,
oxford journals,
ethernet,
Data Privacy Law,
International Data Privacy Law,
Internet businesses,
jurisdictional claims,
market sovereignty,
svantesson,
jurisdictional,
sovereignty’,
destroying,
grotius,
measures’,
Add a tag
By Dan Jerker B. Svantesson
One of the most prominent features of jurisdictional rules is a focus on the location of actions. For example, the extraterritorial reach of data privacy law may be decided by reference to whether there was the offering of goods or services to EU residents, in the EU.
Already in the earliest discussions of international law and the Internet it was recognised that this type of focus on the location of actions clashes with the nature of the Internet – in many cases, locating an action online is a clumsy legal fiction burdened by a great degree of subjectivity.
I propose an alternative: a doctrine of ‘market sovereignty’ determined by reference to the effective reach of ‘market destroying measures’. Such a doctrine can both delineate, and justify, jurisdictional claims in relation to the Internet.
It is commonly noted that the real impacts of jurisdictional claims in relation to the Internet is severally limited by the intrinsic difficulty of enforcing such claim. For example, Goldsmith and Wu note that:
“[w]ith few exceptions governments can use their coercive powers only within their borders and control offshore Internet communications only by controlling local intermediaries, local assets, and local persons” (emphasis added)
However, I would advocate the removal of the word ‘only’. From what unflatteringly can be called a cliché, there is now a highly useful description of a principle well-established at least 400 years ago.

The word ‘only’ gives the impression that such powers are of limited significance for the overall question, which is misleading. The power governments have within their territorial borders can be put to great effect against offshore Internet communications. A government determined to have an impact on foreign Internet actors that are beyond its directly effective jurisdictional reach may introduce what we can call ‘market destroying measures’ to penalise the foreign party. For example, it may introduce substantive law allowing its courts to, due to the foreign party’s actions and subsequent refusal to appear before the court, make a finding that:
- that party is not allowed to trade within the jurisdiction in question;
- debts owed to that party are unenforceable within the jurisdiction in question; and/or
- parties within the control of that government (e.g. residents or citizens) are not allowed to trade with the foreign party.
In light of this type of market destroying measures, the enforceability of jurisdictional claims in relation to the Internet may not be as limited as it may seem at a first glance.
In this context, it is also interesting to connect to the thinking of 17th century legal scholars, exemplified by Hugo de Groot (better known as Hugo Grotius). Grotius stated that:
“It seems clear, moreover, that sovereignty over a part of the sea is acquired in the same way as sovereignty elsewhere, that is, [...] through the instrumentality of persons and territory. It is gained through the instrumentality of persons if, for example, a fleet, which is an army afloat, is stationed at some point of the sea; by means of territory, in so far as those who sail over the part of the sea along the coast may be constrained from the land no less than if they should be upon the land itself.”
A similar reasoning can usefully be applied in relation to sovereignty in the context of the Internet. Instead of focusing on the location of persons, acts or physical things – as is traditionally done for jurisdictional purposes – we ought to focus on marketplace control – on what we can call ‘market sovereignty’. A state has market sovereignty, and therefore justifiable jurisdiction, over Internet conduct where it can effectively exercise ‘market destroying measures’ over the market that the conduct relates to. Importantly, in this sense, market sovereignty both delineates, and justifies, jurisdictional claims in relation to the Internet.
The advantage market destroying measures have over traditional enforcement attempts could escape no one. Rather than interfering with the business operations worldwide in case of a dispute, market destroying measures only affect the offender’s business on the market in question. It is thus a much more sophisticated and targeted approach. Where a foreign business finds compliance with a court order untenable, it will simply have to be prepared to abandon the market in question, but is free to pursue business elsewhere. Thus, an international agreement under which states undertake to only apply market destroying measures and not seek further enforcement would address the often excessive threat of arrests of key figures, such as CEOs, of offending globally active Internet businesses.
Professor Dan Jerker B. Svantesson is Managing Editor of the journal International Data Privacy Law. He is author of Internet and E-Commerce Law, Private International Law and the Internet, and Extraterritoriality in Data Privacy Law. Professor Svantesson is a Co-Director of the Centre for Commercial Law at the Faculty of Law (Bond University) and a Researcher at the Swedish Law & Informatics Research Institute, Stockholm University.
Combining thoughtful, high level analysis with a practical approach, International Data Privacy Law has a global focus on all aspects of privacy and data protection, including data processing at a company level, international data transfers, civil liberties issues (e.g., government surveillance), technology issues relating to privacy, international security breaches, and conflicts between US privacy rules and European data protection law.
Subscribe to the OUPblog via email or RSS.
Subscribe to only law articles on the OUPblog via email or RSS.
Image credit: Ethernet cable with a padlock symbolising internet security. © SKapl via iStockphoto.
The post A doctrine of ‘market sovereignty’ to solve international law issues on the Internet? appeared first on OUPblog.


Over two years ago, before The Only Ones came out, I did a countdown of 99 things (books, movies, art, places, etc.) that inspired it. It was a fun way to revisit some stuff I was actively thinking about when I wrote the book, as well as some stuff I didn’t realize influenced me until I had some time to reflect.
Well, it’s 99 days until The Riverman hits shelves and I figured, why not do it all again? So, without further ado, here is my list of #99inspirations that I’ll be counting down daily on Twitter. This doesn’t represent all of my favorite things (sorry, no bright copper kettles and warm woolen mittens here), though it does include some stuff that I truly love. And hopefully it sparks some conversation about the stuff you love and the stuff that leaks into your creations.

By: KatherineS,
on 2/27/2014
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
terrorism,
terror,
activists,
Al-Qaeda,
chat room,
*Featured,
Science & Medicine,
Psychology & Neuroscience,
community of supporters,
The Social Net,
Understanding our online behavior,
US Department of Defense,
Yair Amichai-Hamburger,
amichai,
Books,
internet,
Politics,
Current Affairs,
social media,
Add a tag
By Yair Amichai-Hamburger
On the Internet, terrorists can find a wide-open playground for particularly sophisticated violence. I have no doubt that the people at the US Department of Defense, when they brought about the inception of the Internet, never thought in their worst nightmares that come 2013, every terrorist splinter group would boast a website and that all the advantages of the Internet would be at the service of terrorists for organizing, planning, and executing their attacks on innocent people.
The Internet helps terror groups in a variety of activities: recruiting members, establishing communication, attaining publicity, and raising funds. Terror organizations direct their messages to their various audiences over the net with great sophistication. The primary audience is the central core of activists, who use the website as a platform for information about various activities. Messages are disguised by pre-agreed codes, and if you’re unfamiliar with the codes, you won’t understand what’s being talked about.

By means of such encoded messages, a global network of terror can operate with great efficiency. It can manage its affairs like an international corporation: the leader passes instructions to various operations officers around the world, and they pass instructions onward to their subordinates. Using the Internet for information transfer, the organization can create a compartmentalized network of activists who cannot identify one another. Even if one cell is exposed, the damage to the overall network is minimal. Ironically, that survivability was exactly the factor that guided the US Department of Defense when it set up the Internet in anticipation of a doomsday scenario.
The second audience that the terror websites speak to is the general community of supporters. Messages for them are open, not disguised, and the operational side is toned down a little. At the site for the general public, the focus is on negative messages regarding the terror organization’s target, and on legitimizing attacks against it without going into specifics. The site presents history in a way that suits its agenda, and often it tries to attract legitimate contributions for its activities by concealing them behind various charitable fronts.
Some of these sites sell souvenirs with the terror organization’s logo, as if it were a sports team. Thus fans can buy scarves or shirts that give them a strengthened sense of identification with the terror organization. The site allows visitors to join discussions, and in some cases it also tries to attract people from the community of true believers into the community of activists. Of course such a process is undertaken with much caution in order that spies not infiltrate the organization. When new volunteers are recruited, there is a great advantage to enlisting people who don’t fit the terrorist stereotype, since such people can serve as couriers without immediately arousing suspicion. On the other hand, the less the new volunteer belongs to the community from which the terror organization sprang, or resembles a member of that community, the greater the suspicion of untrustworthiness. So such a new volunteer will be performing under close watch, or will be assigned to a one-time task that is to end in the grave.
The third audience is the group to be terrorized. In addressing this group, the organization has the objective of arousing fear, and it publicizes its terror operations in order to “win” the audience to the idea that each of them, including their family and closest friends, is likely to be the next terror victim. This baleful message is accompanied by an ultimatum to the audience: if all its demands are not met, the terror organization will make good on all its threats. The terror organization will try to show that because it’s fighting for absolute justice and has no mercy as it makes its way to that goal, it’s unstoppable. It immortalizes its terrorism in well-concocted documentary films that portray successes among its deadly operations, and by documenting executions performed on camera.
Examining the way that terror organizations address their audiences over various channels, we can see that most terror organizations deploy a rather impressive public-relations corps. Many terror organizations, not satisfied with a website alone, expand onto social networks and use other net-based avenues such as e-mail, chats, and forums.
The language of terror is quite interesting. Terrorists lay all the blame on the other party, which they label the aggressor while they present themselves as the real victims who speak in the name of human rights and who champion the oppressed. Take for example the international terror organizations. They explain that terror is the only method they have for striking back defensively at the imperialist aggressor. The terror organizations delegitimize their opponents and describe their enemy as the ultimate aggressor, a perpetrator of criminal actions such as genocide, slaughter, and massacres. Sometimes the fight is considered part of a continuing religious war and the messages bear a religious aura. For instance, a jihad with the prophet Muhammad as the commander in chief, in charge of the courageous legions that the organization represents.
Terror organizations tend to describe their murderous activities as self-defense by a persecuted underdog. They ignore the human side of their victims and use the psychological tool of dehumanization against the opponent, defining it as a group that has no human face. Thus for example, after the attack on the Twin Towers and the Pentagon on 11 September 2001, the Al Qaeda organization completely ignored the thousands of murdered people and chose to focus on the indignities that the capitalist Americans had wreaked, and were continuing to wreak, and on the importance of the Twin Towers as a symbol of the western world’s decadence.
Yair Amichai-Hamburger is Director of The Research Center for Internet Psychology, Israel, and author of The Social Net: Understanding our online behavior. This article originally appeared as part of a series on Psychology Today.
Subscribe to the OUPblog via email or RSS.
Subscribe to only psychology articles on the OUPblog via email or RSS.
Image credit: Fingers on a keyboard, via iStockphoto.
The post Terror appeared first on OUPblog.

These tools will help you keep track of where/when your name and your book title(s) are mentioned on the Internet.
http://www.personalbrandingblog.com/10-must-have-tools-for-tracking-brand-mentions/
Agent Jill Corcoran tells all you need to know about submitting a manuscript digitally.
http://jillcorcoran.blogspot.com/2011/01/how-to-sub-queries-full-ms-in-digital.html
Can you see this post? I’m hearing that some folks can’t get my site to load. Has been a problem all day; we’re looking into it. I’m bumping the Ballet Shoes post yet another day until I’m sure the problem (whatever it is) has been resolved.
Meanwhile, noooooo! Google informs us Reader’s days are numbered. Those of us who rely on a good RSS aggregator to make the web manageable are crushed—there’s no better feed reader than Google Reader.
Some alternatives, none of them quite perfect (but I’m confident someone will rise to fill the void):
Feedly—this is probably what I’ll wind up using. Not quite as streamlined as Reader, but it offers many options for customizing the look and function. In “Full Articles” mode, it’s a decent Reader substitute:
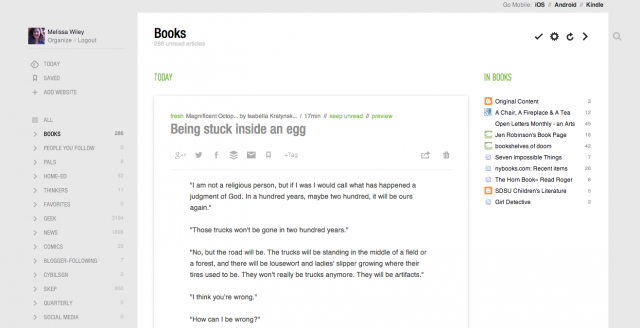
(I subscribe to way more book blogs than are visible in that list. I think it only shows the top twelve.)
If you click on the gear icon, you can toggle to different layouts: mosaic, list, magazine-style, etc.
You can export your subscriptions at Google Reader and import them to Feedly, or simply connect Feedly to your Reader account, which is what I did. For now Feedly runs off Reader’s API but it is going to “seamlessly transition” to another source before Reader bites the dust in July.
A Feedly plus is that it has mobile apps as well, with syncing between your desktop, iOS, and Android devices. And if you connect it to your gReader account, it’ll sync with that, too, as long as gReader lasts.
You can share posts from Feedly directly to Facebook, Twitter, G+, Delicious, and other platforms. Diigo isn’t one of the preset share options and I really hope you can add it manually—haven’t figured out how yet but it’s early days—because Diigo is how I share links in my sidebar here. I suppose I could switch back to Delicious if I have to.
Here’s Feedly in “magazine” view:
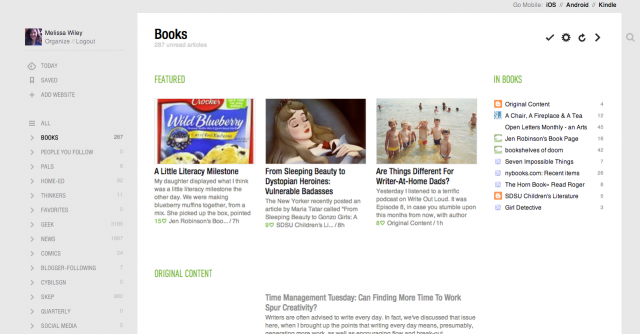
Other options: Bloglines (what I used before Google Reader came along). NewsBlur (after a certain number of subscriptions, there’s a fee). NetNewsWire for Mac. The Old Reader. Pulp (a paid app for Mac). Flipboard for iOS devices (no good for me, as I need a desktop interface).
What’s your poison?
The next time I read a website
I hope it doesn’t disappoint
as significantly as this one.
I mean, I know it was my choice
to read, but I basically thought
youd have something
fascinating
to say.
All I hear is actually
a bunch of whining
about something which you could fix
when you werent too busy
looking for attention.
Sincerely,
Cheap China Jordans
at Best Skilled Care
***
rather nice post
i surely love this webpage
keep on it
Signed,
Cheap China Jordans
at Pointe Pest Control
P.S. Our NFL Jerseys best price
Following up on yesterday’s post—some good questions came up in the comments. I’ll tackle this one first: “How does the Send to Kindle app work?”
Send to Kindle
I mentioned how much I rely on Send to Kindle to read long-form posts and articles later, away from my computer. This is an official Amazon app but there are third-party equivalents, too. (See Send to Reader, below. Instapaper is another.)
How it works: I installed Send to Kindle in my browser. (There are Chrome and Firefox versions, PC and Mac desktop versions, and even an Android app.)
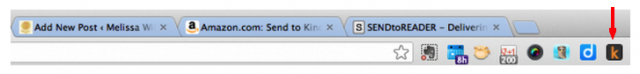
In Chrome, the Send to Kindle icon appears at the top right of my browser—see the orange K?
When I’m reading a post online and I want to send it to my Kindle, all I have to do is click the icon.
If I want, I can choose to send the article to the Kindle app on an iPhone, iPad, or Android device instead. Click the icon to access the settings button. This is handy if I want to send a particular article to Scott’s device instead of mine. (You may have up to six devices connected to your Kindle account at any one time.)

Send to Reader
As I said, Send to Reader works almost the same way. You create an account, install its bookmarklet in your toolbar, and enter your Kindle’s email address. IMPORTANT: Be sure to use the free.kindle.com version of your Kindle address, i.e. [email protected], not [email protected]. This is the simplest way to avoid any download charges for the content you send. (You can also tweak your Kindle document settings to make sure you don’t accidentally download content via Whispernet, incurring data charges. Go to Amazon –> Manage Your Kindle –> Personal Document Settings and set a price limit of, say, one cent for download fees. That way, any download that would exceed that fee will be withheld until you’re connected via Wifi, where all downloads are free. Or just make a point of always using the free.kindle.com address instead!)
While you’re in your Kindle settings, be sure to enter [email protected] as one of your approved email addresses for receiving content.
This fussy set-up stuff takes much more time to describe than to do. Once you’re set up, you don’t have to bother with this ever again. From then on, you can zap articles to your Kindle by simply clicking the bookmarklet.
I believe Send to Reader works with the Kindle app on your iPad or Android device, as well. If you don’t know your device’s Kindle email address, you can find it at Manage Your Kindle –> Personal Document Settings.

Sending posts directly from Google Reader
OK, so that’s how I send long-form web content to my e-reader for perusing later. Now let’s back up half a step: say I’m reading a blog post in Google Reader—how do I send that post to my Kindle? Two ways. Either I can click through to the actual post and follow the steps above, or I can send it directly from Reader via the “Send to” button.
See the “Send to” tab at the bottom of the post? When you click on it, up pop your options. You can send this post all over the place!
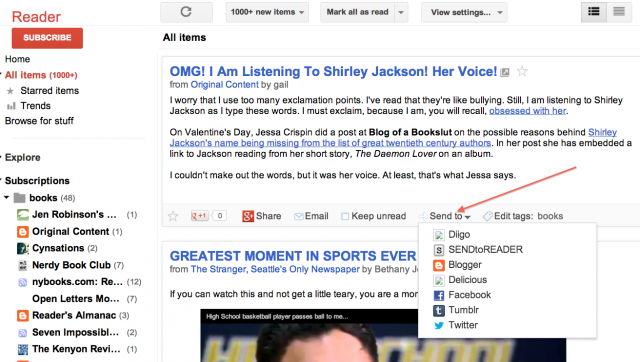
Here’s how to configure the options: In Google Reader, click the Settings gear icon. Select “Reader Settings.”
Click the “Send to” tab to get to the screen pictured below.
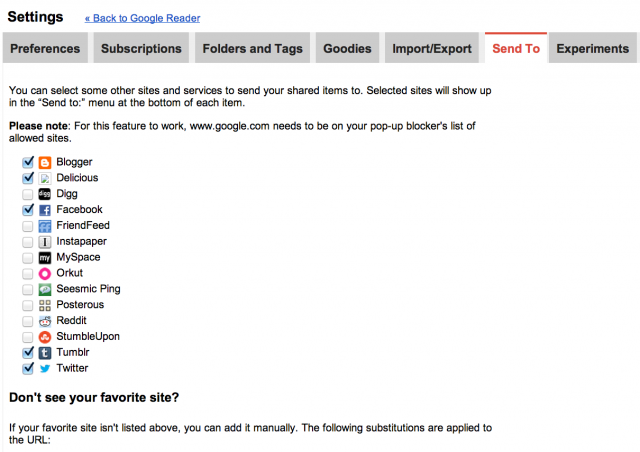
Choose whatever sites you like to send stuff to.
You’ll notice Diigo and Send to Reader are missing from this checklist, but do appear in my list of options in the previous photo. That’s because I added them manually (again, a one-time set-up process) following the instructions under “Don’t see your favorite site?”
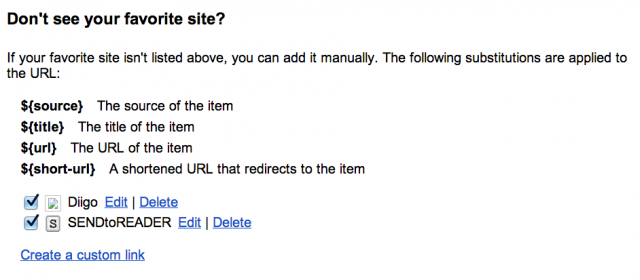
Click “Create a custom link” to connect with the site of your choice. Again, I think this kind of thing is harder to explain than to do. Let me know if anything here doesn’t make sense!
I should add that I really only use Google Reader’s “send to” feature to send articles to my Kindle—I seldom share links to Facebook or Twitter this way. I prefer HootSuite for that. But that is fodder for another post.

By: Kathy Temean,
on 12/3/2012
Blog:
Writing and Illustrating
(
Login to Add to MyJacketFlap)
JacketFlap tags:
News,
Internet,
Random House,
Candlewick,
children writing,
Digital Book World,
Conferences and Workshops,
Barbara Marcus,
Karen Lotz,
Publishing Executives,
Add a tag
 The Biggest Children’s Gathering Yet on Tuesday January 15 we’ll kick off Digital Book World Week with our second-annual Publishers Launch Conference focused on the digital transition in children’s publishing–giving this vital segment the deep and focused consideration it deserves.
The Biggest Children’s Gathering Yet on Tuesday January 15 we’ll kick off Digital Book World Week with our second-annual Publishers Launch Conference focused on the digital transition in children’s publishing–giving this vital segment the deep and focused consideration it deserves.
The major themes of the event are the power of platforms; the challenges of marketing and selling to children in a digital age (including specific case studies for picture books, middle grade and YA books); rethinking children’s book intellectual property and the new ways in which publishers are creating, controlling and licensing IP; and the latest data and critical analysis of what it means.
You can come for just the day, or in a new twist, the DBW Children’s Package adds the opening day of Digital Book World–with general keynotes in the morning, and three more children’s-track sessions in the afternoon, including their exclusive new report from PlayScience on The ABC’s of Kids and E-reading at a package price.
We keep adding to the program www.publisherslaunch.com/2012-2013/launch-kids/program which finishes with a panel including Barbara Marcus of Random House, Karen Lotz of Candlewick, and conference chair Lorraine–but here is some of the diverse and talented group of publishing executives, technologists, innovators, educational specialists and librarians speaking:
Mara Anastas, Simon & Schuster Children’s
Jess Brallier, Pearson/Protropica
Todd Brekhus, Capstone Digital
Gretchen Caserotti, Darien Library
Devereux Chatillon, IP Attorney (Callaway and Zola Books)
Rachel Chou, Open Road Integrated Media
Christian Dorffer, Mindshapes/Magic Town
Deborah Forte, Scholastic Media
Corinne Helman, Harper Children’s
Lisa Holton, Classroom, Inc.
Eric Huang, Penguin (UK)
Carl Kulo, Bowker
Swanna MacNair, Creative Conduit
Kristen McLean, Bookigee
Tina McIntyre, Little, Brown Children’s
Asra Rasheed, Reading Rainbow/RRKidz
Terri Lynn Soutor, Brain Hive
Andrew Sugerman, Disney Publishing Worldwide
Jonathan Yaged, Macmillan Children’s Publishing Group
Our one-day program kicks off Digital Book World Week on Tuesday, January 14 in New York City.
Here is a $200 code: Code: DBW13 Register here (prices go up again on December 8), or use the code PUBLUNCH for a 5 percent discount on any ticket option. Be prepared for sticker shock.
Talk tomorrow,
Kathy
Filed under:
children writing,
Conferences and Workshops,
Internet,
News Tagged:
Barbara Marcus,
Candlewick,
Digital Book World,
Karen Lotz,
Publishing Executives,
Random House 

By:
KidLitReviews,
on 10/30/2012
Blog:
Kid Lit Reviews
(
Login to Add to MyJacketFlap)
JacketFlap tags:
blogging,
forgiveness,
relationships,
Internet,
advice,
Middle Grade,
blogs,
Favorites,
gossip,
soccer,
friendships,
middle grade books,
Guest Post,
redemption,
book blog tours,
diary entries,
bullys,
5stars,
Romeo & Juliet,
Karen Pokras Toz,
school plays,
Library Donated Books,
Grand Daisy Press,
Deana Riddle,
advice columnist,
harris family,
Add a tag
GUEST POST by DOUGLAS “DOOGLE” HARRIS 5 Stars Millicent Marie is NOT My Name Karen Pokras Toz Grand Daisy Press No. Pages: 150 Ages: 8 to 12 .................. .................. ................. Back Cover: Twelve-year-old Millicent Marie does not like her name. After all, she was named for a woman who died more than fifty years ago [...]

By: Nicola,
on 9/7/2012
Blog:
OUPblog
(
Login to Add to MyJacketFlap)
JacketFlap tags:
VSI,
very short introduction,
innovation,
smartphone,
*Featured,
Science & Medicine,
VSIs,
david gann,
mark dodgson,
gann,
internet,
Technology,
Add a tag

Innovation: A Very Short Introduction
By Mark Dodgson and David Gann
The next big thing in innovation lies in the ways we innovate using technology. We’re used to thinking about innovations that are technologies — the computer, the Internet, the laser, and so on. But technology is now being used to produce better innovations than ever before. By better, we mean innovations that meet our personal, organizational, and social requirements in new and improved ways, and aren’t just reliant on the technical skills and imagination of corporate engineers and marketers.
Here’s some examples of what we mean. If you have ever been lucky enough to design and build a home, you would have been confronted by technical drawings that are incomprehensible to anyone but trained architects. Nowadays you can have a computerised model of your house that lets you move around it in virtual reality so that you get a high fidelity sense of the layout and feel of rooms. You get to know what it really will look like, and make changes to it, before a brick is laid.

Move up a level and consider the challenges confronting the redesign of Cannon Street station in London. This project involved not only redesigning the station, but also building an office block above it, whilst maintaining access to the fully operational Underground station beneath it. The project used augmented reality technology to assist the design and planning process. Using a smartphone or tablet, augmented reality overlays a digital model on the surrounding real world, so you can see hidden infrastructure such as optical fibers, sewers, and gas lines — and get a sense of what things will look like before work begins. This is especially valuable for dealing with various vintages of infrastructure in busy city environments and when there are concerns about maintaining the integrity of listed buildings.
The key principle in these examples is that non-specialists can become involved in decisions that were previously only made by experts.
Other technologies that encourage this ‘democratization’ of innovation include rapid prototyping. This technology changes the economics of manufacturing, so it becomes feasible to make bespoke, individualized products cheaply. If you design something yourself, you don’t need expensive molds, dies, and machine tools to make it. We are quickly developing technologies that can produce your designs on the spot on your desk.
The Internet underlies much of the advance in the ways we innovate. It allows us to collect information from a massively increased population of designers, producers and users of innovation. It connects ideas, people and organizations. Also important is the ‘Internet of things’ that is the vast number of mobile devices and sensors that are connected together and produce data that can be valuably used to make better decisions. Drivers’ mobile phones, for example, can locate cars and traffic jams and allow better planning of transport flows. We have it from a reputable source that more transistors — the building blocks of sensors and mobile devices — were produced last year than grains of rice were grown. And they were produced at lower unit cost.
We’re all much better attuned at processing images rather than text and data. Half our cerebral cortex is devoted to visualization. Technologies developed in the computer games and film industries — think Toy Story and World of Warcraft — are being used to help innovators in areas ranging from pharmaceuticals to emergency response units in cities. The capacity, which these new technologies bring to produce dynamic images of what was previously opaque technical information, underlies the greater engagement in innovation by a wider range of people.
The technology that seems likely to have the greatest impact globally on innovation is the smartphone. Just think how short a period of time we’ve been using them and yet how much we use them for. Quite apart from putting us in direct contact with the majority in the world’s population, we use them to shop, bank, pay bills, and map our way. We use a myriad of apps for all sorts of productive and entertaining purposes. Nearly 6 million of the world’s 7 million people have mobile phones and in many developing countries there are more mobiles than people.
These devices provide opportunities for innovation amongst billions of people that have previously been excluded from the global economy for lack of information and money. Smartphones provide everyone with access to all the staggering amount of information available on the web. They can also allow access to finance, especially small amounts of money. Less than 2 million people in the world have bank accounts and banking on smartphones allows billions of previously disenfranchised people to borrow, trade, and be reimbursed for their ideas and initiative. In this way, technology makes innovation more inclusive and less the privilege of corporations with research and development departments. We look forward to a massive wave of exciting new and unimaginable ideas from all sorts of people from everywhere around the world.
Mark Dodgson is Director of Technology and Innovation Management Centre, University of Queensland Business School, and David Gann is Head of Innovation and Entrepreneurship at Imperial College London. They co-authored Innovation: A Very Short Introduction.
Subscribe to the OUPblog via email or RSS.
Subscribe to only VSI articles on the OUPblog via email or RSS.
View more about this book on the 

Image credit: Above Cannon St Station, London, by Tom Morris (Creative Commons License). Source: Wikimedia Commons.

September is a busy month for Cole Stryker, the Web's resident authority on all things anonymous. This week brings the paperback release of Stryker's 2011 debut, Epic Win for Anonymous, the first book to tell the full story of 4chan and the rogue antisecurity groups currently changing the world, and on September 13th Overlook will be releasing Cole's highly-anticipated follow up Hacking the
Recently my blogging buddy, Cecelia Lester, passed along to me and a few other bloggers the Liebster Award.
I am such a forget ninny sometimes that I forgot the thank her for that.
So, A BIG THANK YOU! to Cecelia for honoring me as one of her favorite bloggers. You can read Cecelia's beautiful, sincere devotionals at her blog, Following My King. Her heartfelt words often reach out across
_____________________________________________________________________________
The recent, latest online activism against an online idiot encouraged me to write something which I had been thinking about for awhile.
The philosophical musing began when I discovered the following on Wikipedia:
Eternal September
From Wikipedia, the free encyclopedia
Eternal September (also September that never ended)[1] is the period beginning September 1993,[2] a date from which it is believed by some that an endless influx of new users (newbies) has degraded standards of discourse and behavior on Usenet and the wider Internet.
The term eternal September is a Usenet slang expression, and was coined by Dave Fischer. The term is so well entrenched that one news server calls itself Eternal September, and gives the date as a running tally of days since September of 1993 (e.g., Sep. 03, 2012 is “September 6943, 1993, the September that never ends.”).[3] This server was formerly named Motzarella.org.[4]
[edit] Background
Usenet originated among American universities, where every year in September, a large number of new university freshmen acquired access to Usenet for the first time, and took some time to acclimate to the network’s standards of conduct and “netiquette“. After a month or so, these new users would theoretically learn to comport themselves according to its conventions, or simply tire of using the service. September thus heralded the peak influx of disruptive newcomers to the network.[1]
Around 1993, the online services such as America Online, CompuServe and Demon Internet began offering Usenet access to its tens of thousands, and later millions, of users. To many “old-timers”, these newcomers were far less prepared to learn netiquette than university students. This was in part because the new services made little effort to educate their users about Usenet customs, or to explain to them that these new-found forums were outside their service provider’s walled garden, but it was also a result of the much larger scale of growth. Whereas the regular September freshman influx would quickly settle down, the sheer number of new users now threatened to overwhelm the existing Usenet culture’s capacity to inculcate its social norms.[5]
Since that time, the dramatic rise in the popularity of the Internet has brought a constant stream of new users. Thus, from the point of view of the pre-1993 Usenet user, the regular “September” influx of new users never ended. The term was used by Dave Fischer in a January 26, 1994, post to alt.folklore.computers, “It’s moot now. September 1993 will go down in net.history as the September that never ended.”[6]
Some ISPs have eliminated binary groups (Telus in Canada)[7] and others have dropped Usenet altogether (Comcast,[8] AT&T[9], AOL[10][11]). This led some commentators to claim that perhaps September is finally over.[12][13]
——
I was a university student who used the Internet before AOL, Compuserve, and the World Wide Web caused the beginning of the “Eternal September”. I had to learn netiquette. Even when AOL and other online services began to link to the Internet, the users were still paying to use those services, and could be identified, even if they used a screenname (usually required, because of a limit on length) or an account number (CompuServe).
Now? Anyone can go online, create an pseudonymous email account, and post away. If one account is blocked, another can be created.
So, how do you make the Internet a better place for polite discourse? You probably can’t. But here are some possibilities:
1. Hardwire metadata into each online transaction. A person’s location, the connections used, the computer’s identification number… Sure, these can be spoofed via proxies and offshore servers, but you make that a legal requirement, and thus give authorities another tool for prosecution. System administrators can block problem users, and report them to a central agency, in much the same way banks report individuals to credit bureaus. The user would be notified, and an appeal process would be available. Of course, the electronic evidence trail would be quite specific and damning. If a computer is blocked but used by various people, (such at a university or family) then the owner would be required to discipline the user.
1.5 Allow internet users, via various Internet services, to automatically block anyone with a suspect reputation. An individual could even filter by various criteria. Just as Google Chrome warns of suspicious sites, so could social media sites issue a warning when receiving email, instant messages, or other communications from irreputable individuals or computers (such as boiler room scams).
2. Pseudonyms are sometimes required. An individual might be at danger for posting information to the Internet which a government might consider seditious. A person might have created a following on another website and become known by that screen name, just like a writer is known by a pen name.
3. The Internet comment system is the electronic equivalent of a newspaper’s “letters to the editor” column. While it is difficult to monitor comments on every article or web page, there can be alternatives. Comment feeds can allow readers to rate other comments, and the comment system can hide or promote accordingly. If the system is widespread, and uses services such as Facebook, Google, Disqus, Twitter or Yahoo for a commenter to login, then those systems can track the reputation of the user. Of course, this can be abused if others bully a specific user, but then those individual can be identified as well. (The system can even be programmed to check for people who stalk or bully an individual repeatedly.)
4. Teach children the importance and responsibility of writing. “Don’t write anything you don’t want being read in public” was a common warning back when that only meant paper and pen. Now with instant caching and searching, it’s an even more critical skill. Teach students how to write clearly, how to argue and debate politely (if deviously), and how to avoid being viewed as a jerk.
—
I don’t know what the future holds. The Internet makes it so easy to find information, but it also makes it extremely easy to preach to the choir, to avoid anything which might shatter a fantasy or belief. I would hope that extremes would be mitigated, in much the way they were a century ago when local newspapers would promote specific agendas without advocating extremes.
I don’t know if that will change. Some big event, like Oklahoma City, fomented by extremists, won’t make an impact (we didn’t learn the lesson then, and politics has become even more partisan since). Most likely, it will require a lot of different interests working together to make a positive change, but when no one is listening to anyone else, how do get people to work together? Maybe interfaith initiatives can provide some guidance, but the problem with being a peacemaker is that you usually get shot from both sides of the battlefield.
Myself, I’ll continue to (try to) be tolerant and calm when confronted by impassioned commentary. (Most of the time, I just walk away and ignore, refusing to read comments on Yahoo News, for example.) It’s not easy, but life rarely is.
Now, I’m allowing comments, so be polite, intelligent, and understanding. Constructive criticism is welcomed, and I enjoy discourse if it makes me think.
Abusive attacks via Twitter aren’t new, but have certainly increased in media visibility over the past few months. Racist and sexist comments and threats have been detailed repeatedly in the mainstream press recently, often aimed at various prominent people in society. It also exists on a personal level, sadly, with personal attacks and bullying on the rise online.
And sadly, this is true for the comics industry as well. I hadn’t been aware of this myself, but today Ron Marz alerted his followers to one twitter user in particular, who has for the past few months been anonymously attacking prominent women in the industry with gender-specific abuse and threats. Writers, artists and journalists have all targeted by this poster over an extended period of time, whose attacks tend to refer back to rape, submission and misogyny at every opportunity. These were explicit threats made to women simply because they were women.
Mark Millar was one of those who saw Marz’s call for awareness, and made a post to his Millarworld forum in which he not only detailed the comments, but also made plans to take a stand against them. Asking for legal advice and people affected by the poster to step forward, several people contacted Millar via twitter and his message board with what could be done about the comments.
Following which, he posted again later today, explaining that he has contacted a lawyer with a view to taking legal action against this poster – who has used various accounts over the past few months to attack people, but left behind an IP trail. The police, Millar says, have been informed, and will now be following up on this. Action will be taken within the next few days.
The threats are misogynistic in the extreme. I won’t link to them.
It’s a reminder that while abuse does exist online, they come from the minority voice. For every person who decides to use the internet to try and threaten other people, there are tens of thousands of other people who won’t tolerate prejudice. If you ever find yourself to be a victim of online abuse, please do not suffer it in silence. Let other people know.
By Steve Morris
Tonight, Chicago will see the presentation of The 2012 Hugo Awards, at the Hyatt Regency Grand Ballroom. With categories for comics, television, novellas, fanzines and more, the only medium apparently not represented this year will be websites. Hmph! That aside, the Hugos are one of the more prestigious sci-fi awards available, having been active since the 1950s. It will doubtless be a great night for all concerned. Especially the winners!
Tonight will see writers like Bill Willingham and Mike Carey valiantly battle each other for ‘Best Graphic Story’, while Community attempts to wrest ‘Best Dramatic Presentation, Short Form’ from the all-conquering Dr Who. All for this year’s lovely trophy, designed by Deb Kosiba.

The full list of categories and nominees can be found on their website.
Most notably, however, this year’s ceremony will also be livestreamed and liveblogged, so you can follow along at home. The ceremony starts at 8PM CDT, tonight, and will be hosted by blogger (and previous Hugo winner) John Scalzi. Go watch! And don’t forget to cheer on poor Neil Gaiman as he attempts to improve his win-loss ratio.

By: Kathy Temean,
on 7/31/2012
Blog:
Writing and Illustrating
(
Login to Add to MyJacketFlap)
JacketFlap tags:
Events,
How to,
children writing,
demystify,
Query letter,
Internet,
writing,
submissions,
opportunity,
Agent John Cusick,
Sci-Fi and Fantasy,
Writer's Digest Webinar,
Add a tag
 Last week I had dinner in NYC with Agent John Cusick from the S©ott Treimel NY Literary Agency. He told me about the live Webinar he is doing with Writer’s Digest on August 9th at 1pm. It is titled, Writing and Selling Sci-Fi & Fantasy for Kids and Teens. Since this is a hot genre and the fact that John did a fabulous job with the workshops he ran in June, I thought I would pass this information on to all of you Sci-Fi/Fantasy authors.
Last week I had dinner in NYC with Agent John Cusick from the S©ott Treimel NY Literary Agency. He told me about the live Webinar he is doing with Writer’s Digest on August 9th at 1pm. It is titled, Writing and Selling Sci-Fi & Fantasy for Kids and Teens. Since this is a hot genre and the fact that John did a fabulous job with the workshops he ran in June, I thought I would pass this information on to all of you Sci-Fi/Fantasy authors.
Event Date: Thursday, August 9, 2012
Event Time: 1:00 p.m. EDT
Duration: 90 minutes
Cost $89
Each registration comes with access to the archived version of the program and the materials for one year. You do not have to attend the live event to get a recording of the presentation. In all WD webinars, no question goes unanswered. Attendees have the ability to chat with the instructor during the live event and ask questions. You will receive a copy of the webinar presentation in an e-mail that goes out one week after the live event. The answers to questions not covered in the live presentation will be included in this e-mail as well.
ABOUT THE CRITIQUE
All registrants are invited to submit a query letter for their novel. Every query is guaranteed a written critique by instructor John M. Cusick within 60 days of receipt. John reserves the right to request manuscripts or sample chapters from attendees by e-mail following the event.
ABOUT THE WEBINAR
Young adult and middle grade are two of the fastest growing and most robust fiction genres in publishing. These juvenile categories have a tradition of fantasy and sci-fi narratives that continues today with wizards, vampires, and clockwork princesses. The young adult and middle grade markets are rich with imaginative and fantastical stories, worlds, and characters.
What makes some stories stand out, and others unsuccessful, cliché, or—worst of all—left buried in the slush pile? How can you refine your craft to create novels at once lasting and fresh? How does writing for kids and teens differ from writing for adults? How can you capture the attention of an agent in this rich and extremely competitive market? In other words, how can you give your story the best chance to get published?
In this webinar, John M. Cusick will answer these questions and more, using his experience as a literary agent, author, and editor to explore the art and business of writing. This invaluable course with an industry insider will help authors open new doors in their craft and career.
WHAT YOU’LL LEARN:
•How to write for young people—capturing the voice, narration, story, and style
•How to use tropes, myths, and archetypal story structures to create striking, unforgettable fantasy & sci-fi tales
•How to craft detailed, unique, engrossing worlds, full of history and depth
•How to bring to life layered and compelling heroes, anti-heroes, villains, and antagonists
•How to avoid cliché and trend-chasing, and create wholly fresh, standout novels
•How to win the interest of an agent in this competitive market.
INSTRUCTOR
John M. Cusick knows the business from both sides, as a literary agent for young adult and middle grade fiction at Scott Treimel NY, and as a young adult author. His debut novel, Girl Parts, was published by Candlewick Press in 2010, and his much-anticipated follow-up, Cherry Money Baby, is slated for 2013. His clients include debut novelists and veteran authors. John has lectured for the Society of Children’s Book Writers and Illustrators, the Writers’ League of Texas, and for Utah’s Writing and Illustrating for Young Readers. His pieces on writing for teens have appeared in Writer’s Market, The New Inquiry, and on mu
View Next 25 Posts





















 The Biggest Children’s Gathering Yet on Tuesday January 15 we’ll kick off Digital Book World Week with our second-annual Publishers Launch Conference focused on the digital transition in children’s publishing–giving this vital segment the deep and focused consideration it deserves.
The Biggest Children’s Gathering Yet on Tuesday January 15 we’ll kick off Digital Book World Week with our second-annual Publishers Launch Conference focused on the digital transition in children’s publishing–giving this vital segment the deep and focused consideration it deserves.


 Last week I had dinner in NYC with Agent John Cusick from the S©ott Treimel NY Literary Agency. He told me about the live Webinar he is doing with Writer’s Digest on August 9th at 1pm. It is titled, Writing and Selling Sci-Fi & Fantasy for Kids and Teens. Since this is a hot genre and the fact that John did a fabulous job with the workshops he ran in June, I thought I would pass this information on to all of you Sci-Fi/Fantasy authors.
Last week I had dinner in NYC with Agent John Cusick from the S©ott Treimel NY Literary Agency. He told me about the live Webinar he is doing with Writer’s Digest on August 9th at 1pm. It is titled, Writing and Selling Sci-Fi & Fantasy for Kids and Teens. Since this is a hot genre and the fact that John did a fabulous job with the workshops he ran in June, I thought I would pass this information on to all of you Sci-Fi/Fantasy authors.
Hahahahahahaha thank you for the laugh!!! It is so frustrating when the internet is down or as in our case running so very slow. Good luck I hope the family calls you soon. 😊😊
I followed the bread crumbs and made it home after the repairman came out. Such a first world problem, but so huge for teenagers.
i have lived this mark, and you made me spit my coffee, (luckily not onto my laptop). it is such a frustrating process trying to get help and unfortunately i am truly ‘tech challenged’ so it’s not a good combination. i think you did exactly the right thing in the end )
Hey I feel the pain of your children. When we moved and it was going to take 2 freaking weeks before they could set us up at our new abode I spent a lot of time in coffee shops until DH got me this thingy that let me connect. It was pricey but he said his safety was worth it :)
…
…
“Girls, how can we make the best of this gift?”
Tech Support Weenie…:D I figured it out: You need a morning radio show, Mark. It’ll go big! Use the LIP brand–it’ll work!